Benefits of Edge Computing

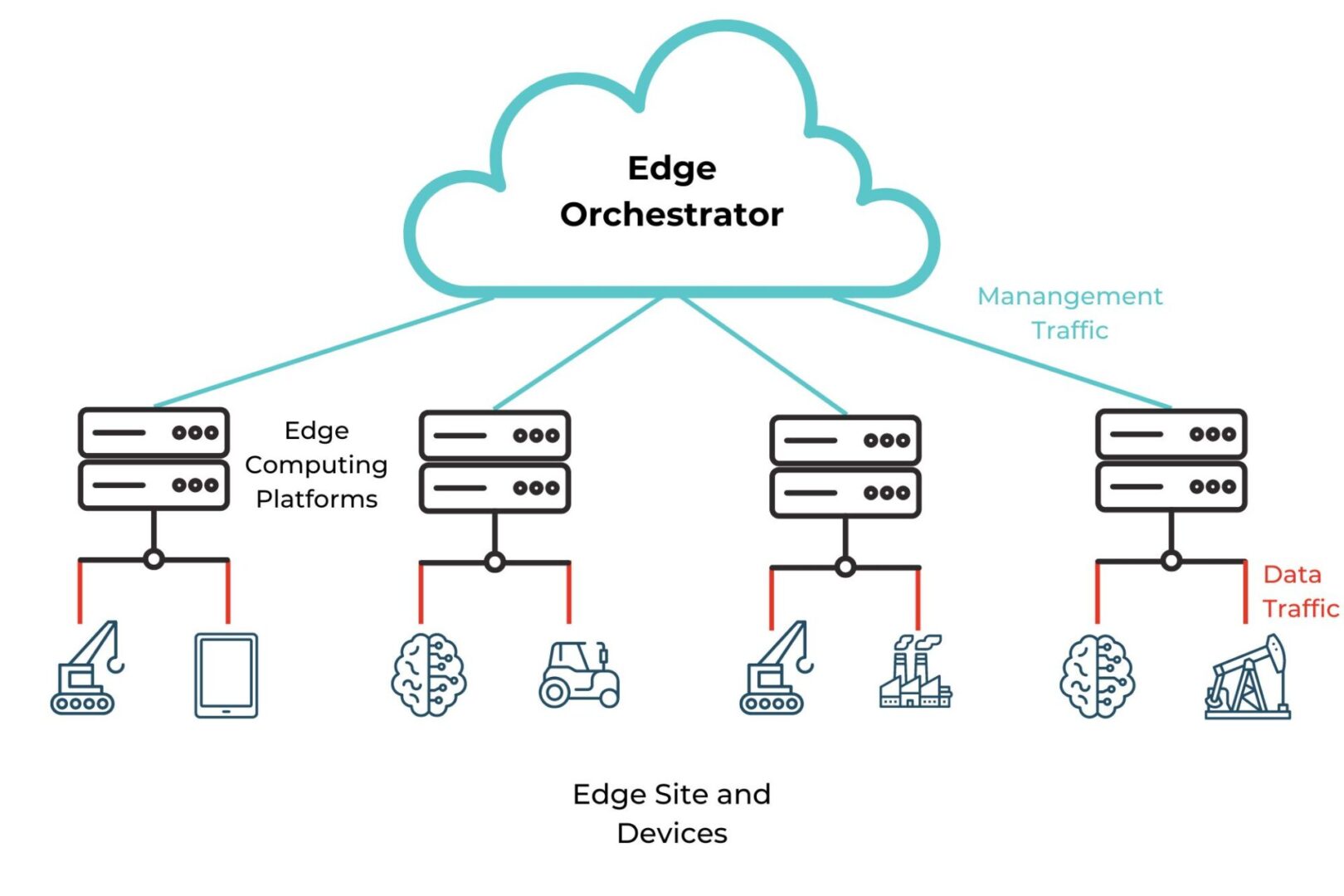
Edge computing delivers data processing and analysis capabilities to the network’s “edge,” at remote sites like branch offices, warehouses, retail stores, and manufacturing plants. It involves deploying computing resources and lightweight applications very near the devices that generate data, reducing the distance and number of network hops between them. In doing so, edge computing reduces latency and bandwidth costs while mitigating risk, enhancing edge resilience, and enabling real-time insights. This blog discusses the five biggest benefits of edge computing, providing examples and additional resources for companies beginning their edge journey.
.
5 benefits of edge computing
1. Reduces latency
Edge computing leverages data on the same local network as the devices that generate it, cutting down on edge data transmissions over the WAN or Internet. Reducing the number of network hops between devices and applications significantly decreases latency, improving the speed and performance of business intelligence apps, AIOps, equipment health analytics, and other solutions that use edge data.
Some edge applications run on the devices themselves, completely eliminating network hops and facilitating real-time, lag-free analysis. For example, an AI-powered surveillance application installed on an IoT security camera at a walk-up ATM can analyze video feeds in real-time and alert security personnel to suspicious activity as it occurs.
2. Mitigates risk
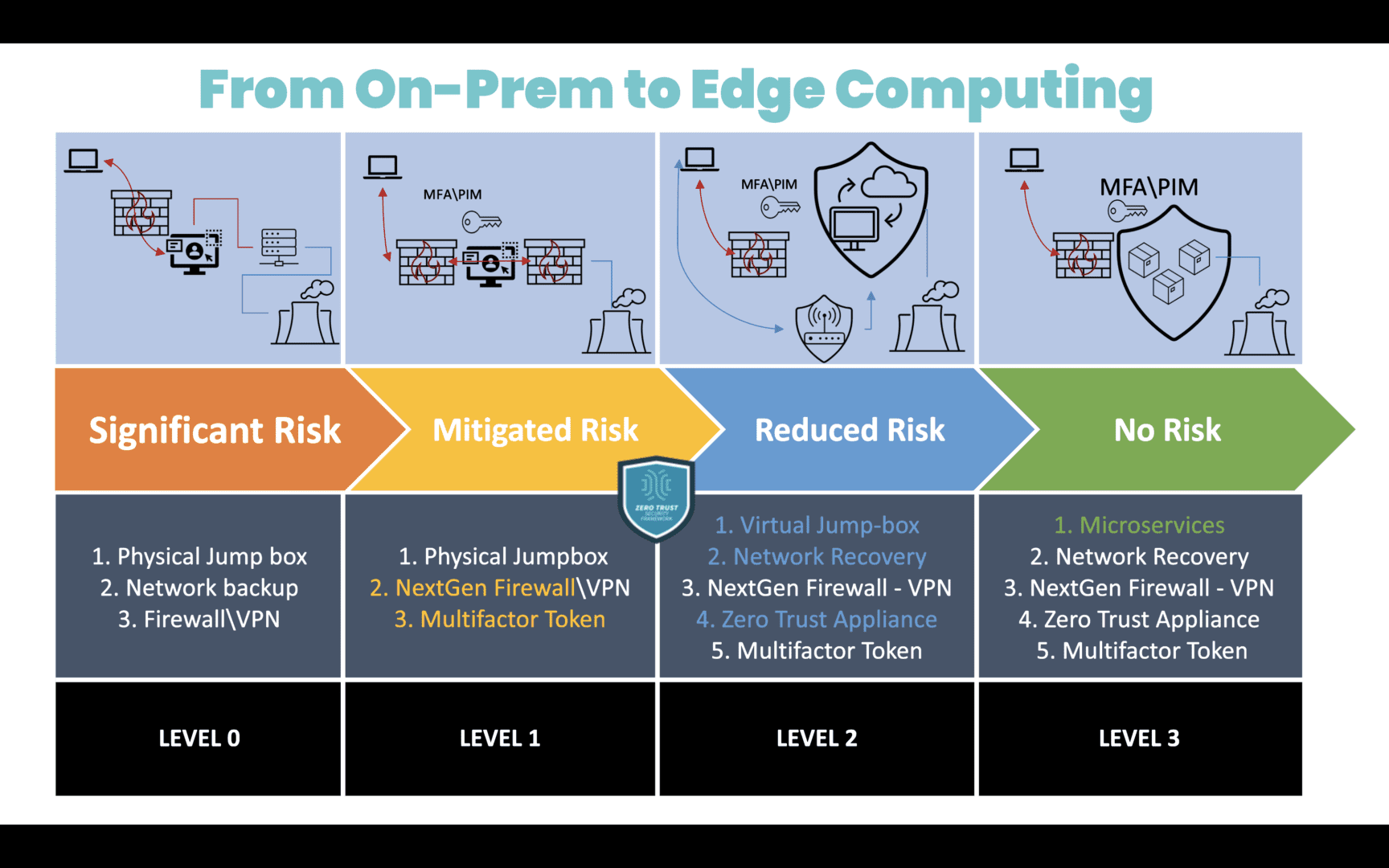
Edge computing mitigates security and compliance risks by distributing an organization’s sensitive data and reducing off-site transmission. Large, centralized data stores in the cloud or data center are prime targets for cybercriminals because the sheer volume of data involved increases the chances of finding something valuable. Decentralizing data in much smaller edge storage solutions makes it harder for hackers to find the most sensitive information and also limits how much data they can access at one time.
Keeping data at the edge also reduces the chances of interception in transit to cloud or data center storage. Plus, unlike in the cloud, an organization maintains complete control over who and what has access to sensitive data, aiding in compliance with regulations like the GDPR and PCI DSS 4.0.
.
3. Lowers bandwidth costs
Many organizations use MPLS (multi-protocol label switching) links to securely connect edge sites to the enterprise network. MPLS bandwidth is much more expensive than regular Internet lines, which makes transmitting edge data to centralized data processing applications extremely costly. Plus, it can take months to provision MPLS at a new site, delaying launches and driving up overhead expenses.
Edge computing significantly reduces MPLS bandwidth utilization by running data-hungry applications on the local network, reserving the WAN for other essential traffic. Combining edge computing with SD-WAN (software-defined wide area networking) and SASE (secure access service edge) technologies can markedly decrease the reliance on MPLS links, allowing organizations to accelerate branch openings and see faster edge ROIs.
.
4. Enhances edge resilience
Since edge computing applications run on the same LAN as the devices generating data, they can continue to function even if the site loses Internet access due to an ISP outage, natural disaster, or other adverse event. This also allows uninterrupted edge operations in locations with inconsistent (or no) Internet coverage, like offshore oil rigs, agricultural sites, and health clinics in isolated rural communities. Edge computing ensures that organizations don’t miss any vital health or safety alerts and facilitates technological innovation using AI and other data analytics tools in challenging environments..
.
5. Enables real-time insights
Sending data from the edge to a cloud or on-premises data lake for processing, transformation, and ingestion by analytics or AI/ML tools takes time, preventing companies from acting on insights at the moment when they’re most useful. Edge computing applications start using data as soon as it’s generated, so organizations can extract value from it right away. For example, a retail store can use edge computing to gain actionable insights on purchasing activity and customer behavior in real-time, so they can move in-demand products to aisle endcaps or staff extra cashiers as needed.
.
Simplify your edge computing deployment with Nodegrid
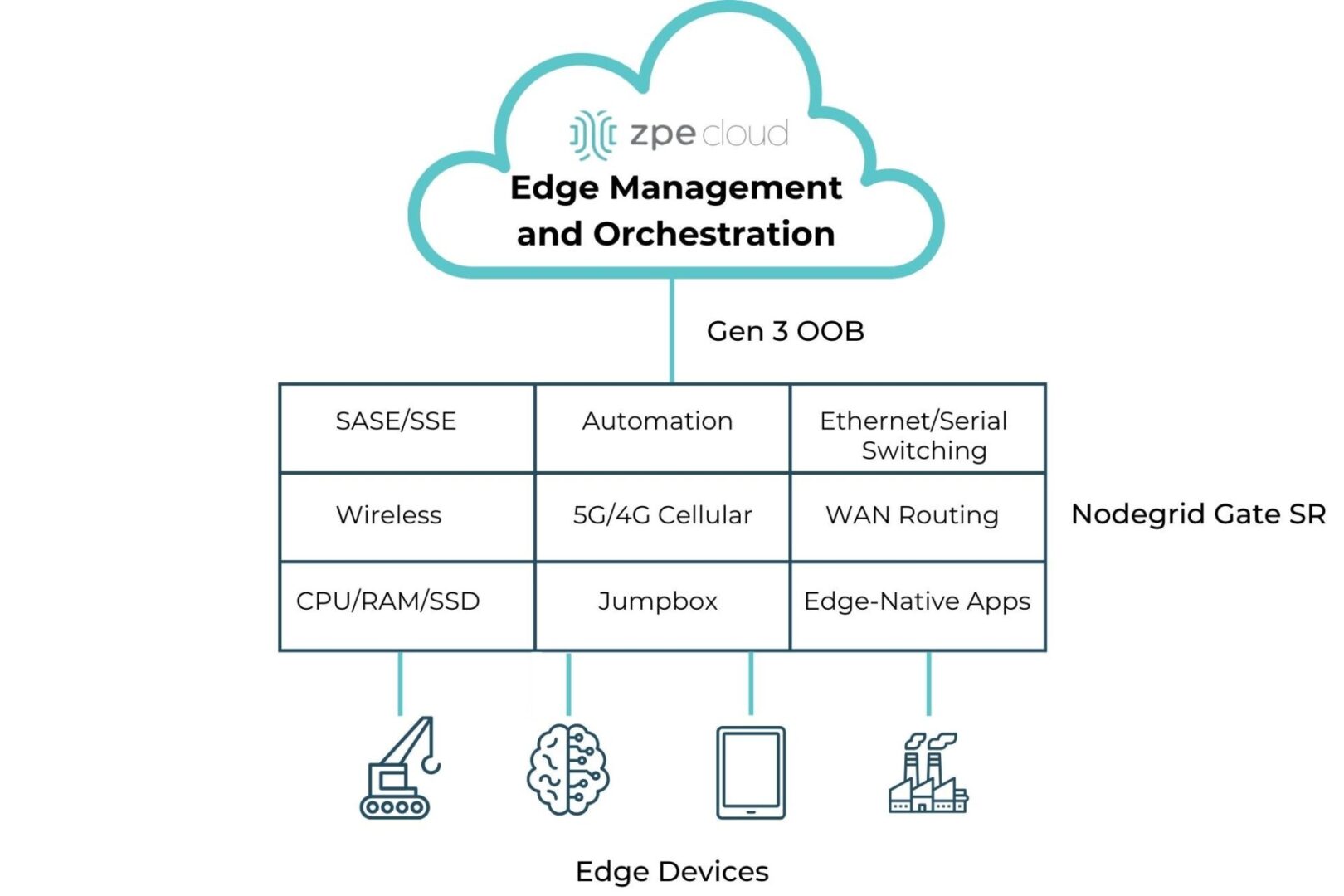
The best way to achieve the benefits of edge computing described above without increasing management complexity or hardware overhead is to use consolidated, vendor-neutral solutions to host, connect, and secure edge workloads. For example, the Nodegrid Gate SR from ZPE Systems delivers an entire stack of edge networking and infrastructure management technologies in a single, streamlined device. The open, Linux-based Nodegrid OS supports VMs and containers for third-party applications, with an Nvidia Jetson Nano card capable of running AI workloads alongside non-AI data analytics for ultimate efficiency.
Improve your edge computing deployment with Nodegrid
Nodegrid consolidates edge computing deployments to improve operational efficiency without sacrificing performance or functionality. Schedule a free demo to see Nodegrid in action.

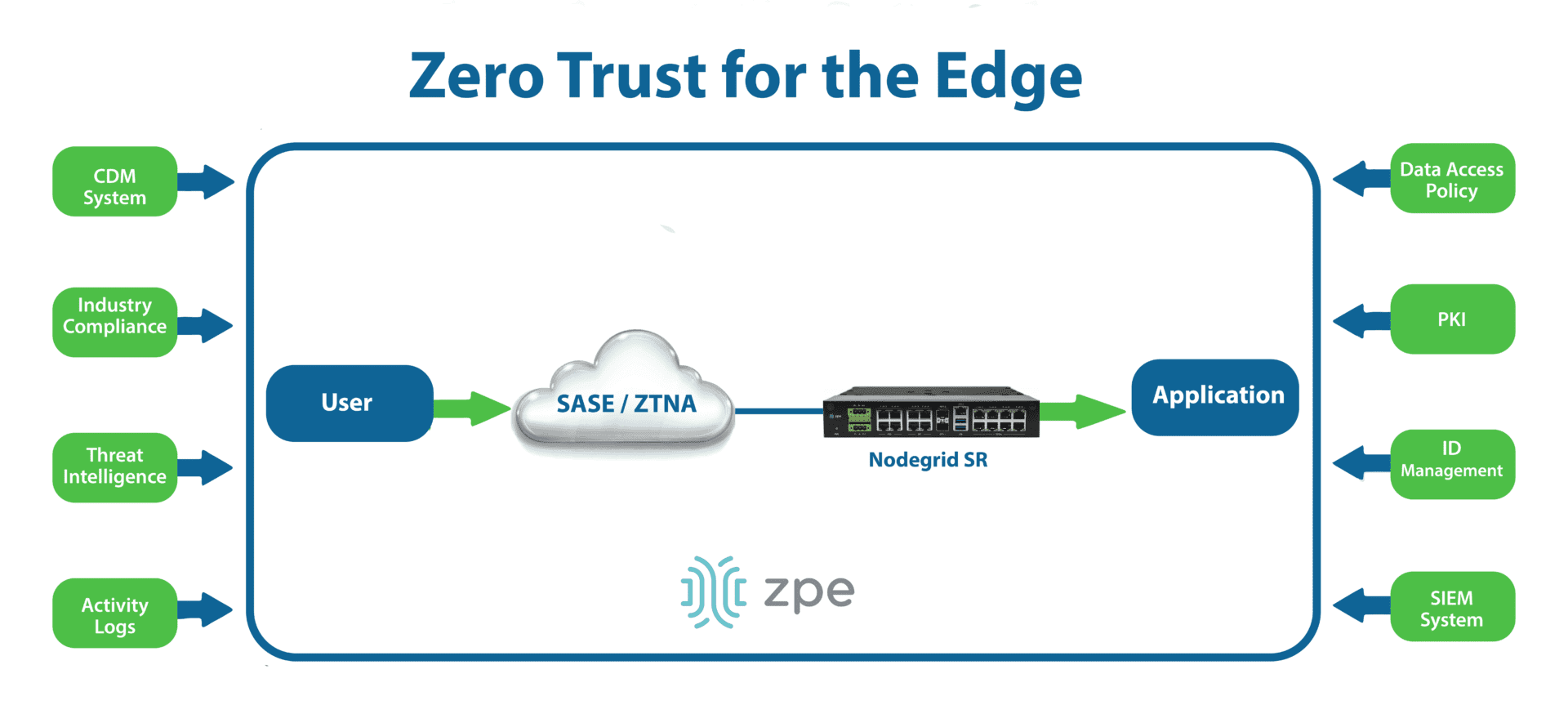
 The easiest and most secure way to implement IMI is with
The easiest and most secure way to implement IMI is with 
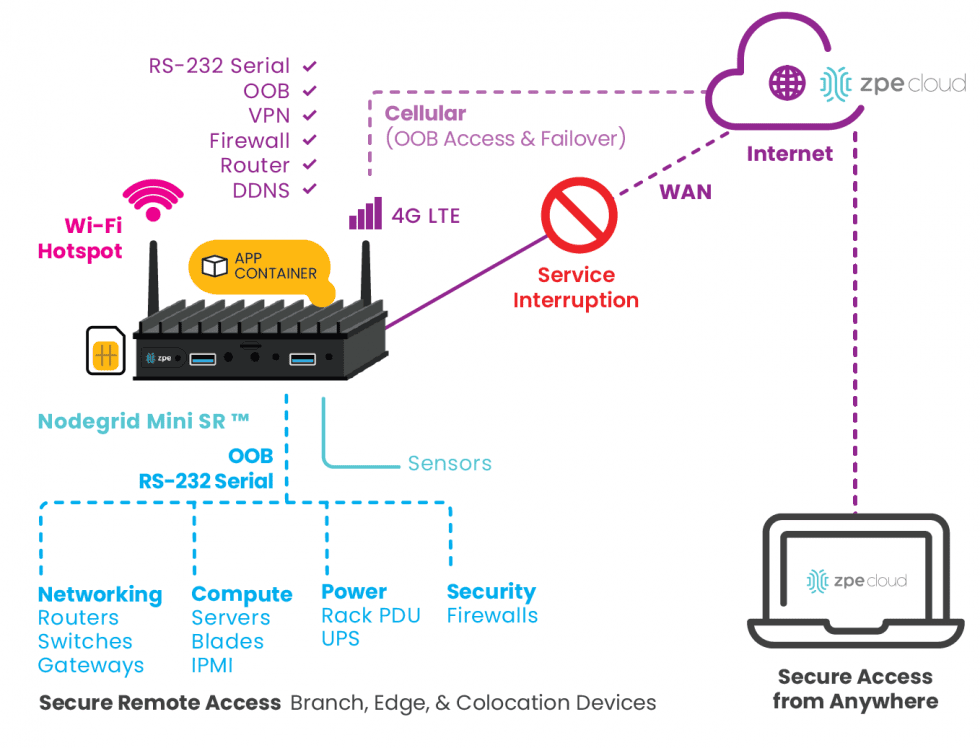
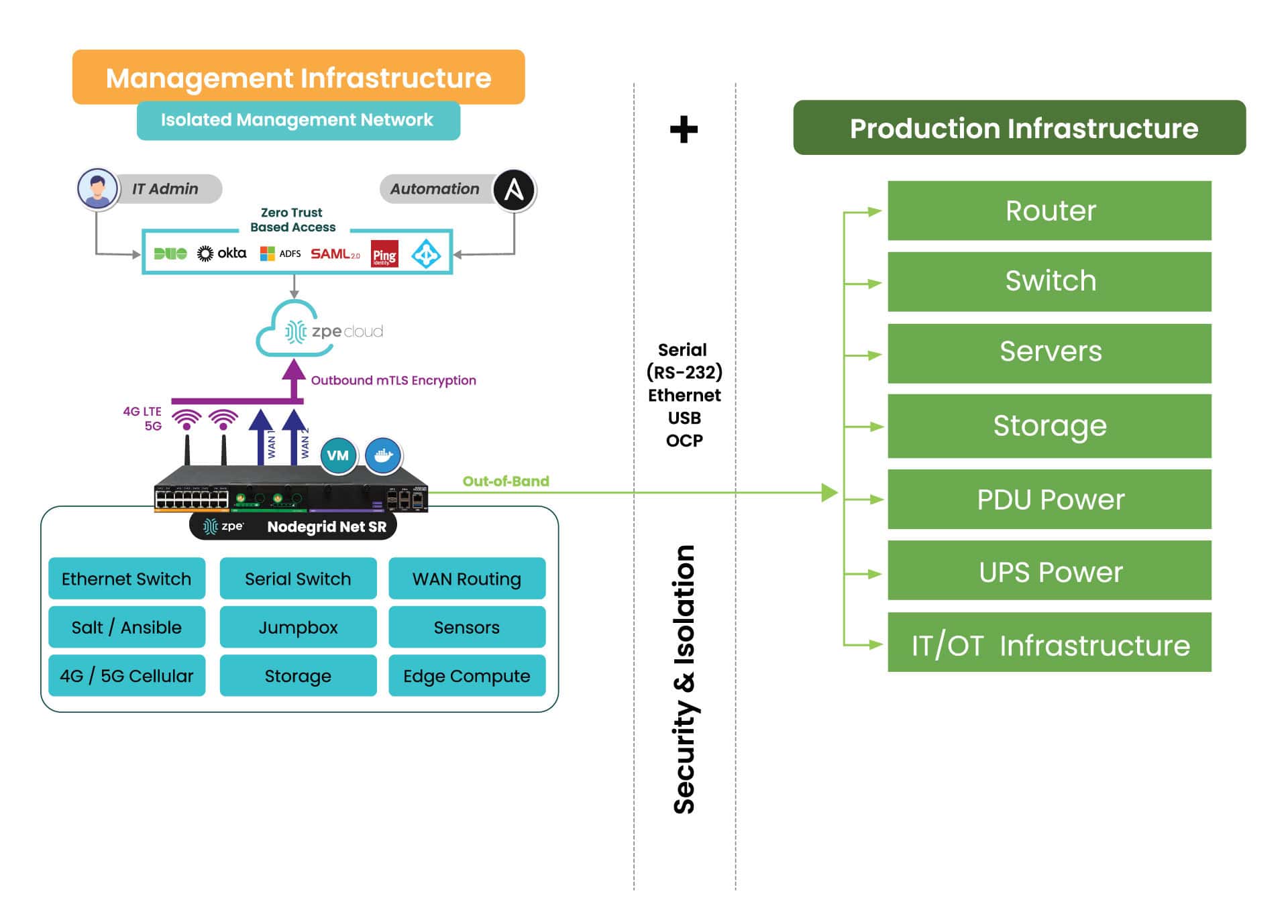
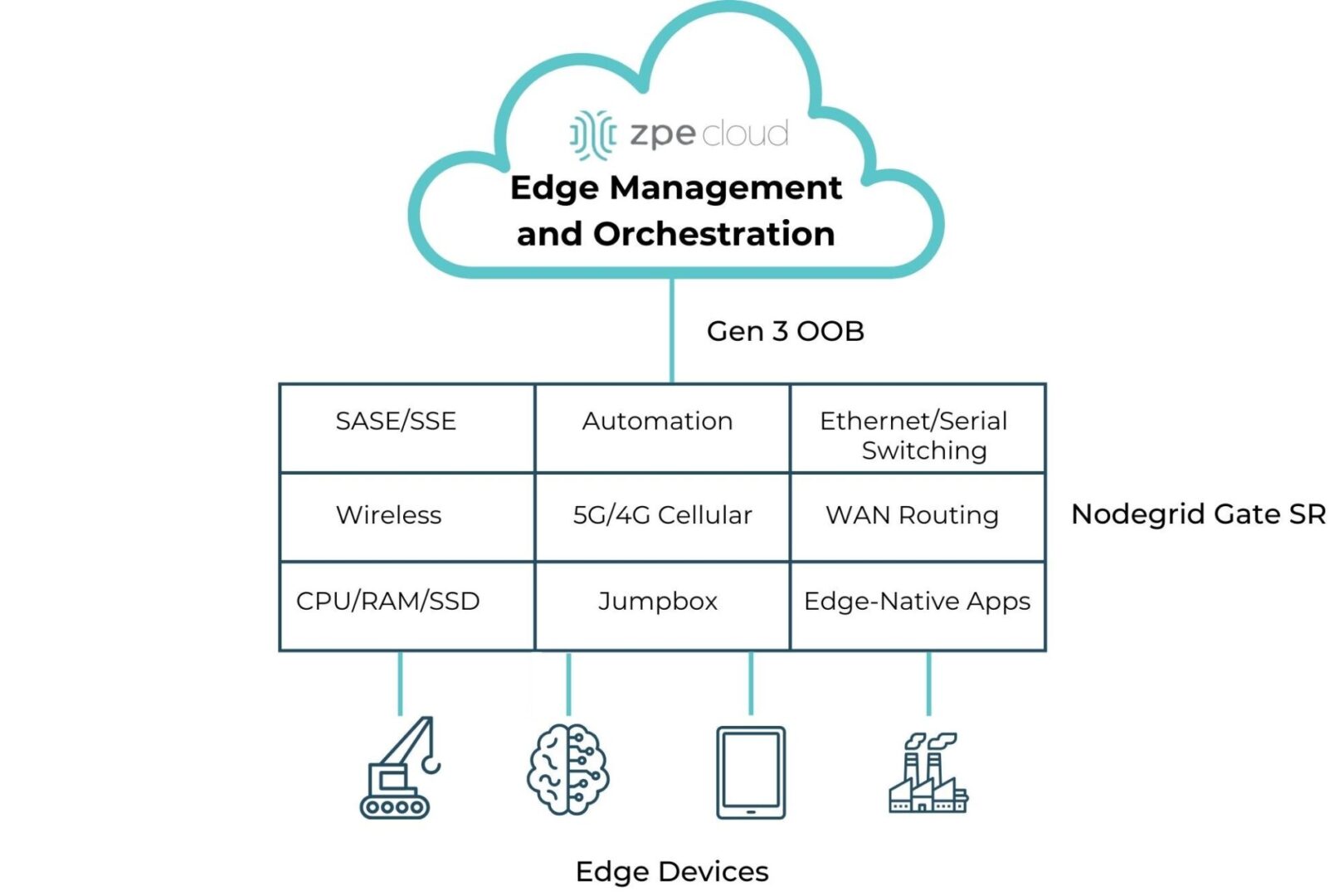 Nodegrid’s OOB also ensures remote teams have 24/7 access to manage, troubleshoot, and recover edge deployments even during a major network outage or ransomware infection. Plus, Nodegrid’s ability to host Guest OS, including Docker containers and VNFs, allows companies to consolidate an entire edge networking stack in a single platform. Nodegrid devices like the
Nodegrid’s OOB also ensures remote teams have 24/7 access to manage, troubleshoot, and recover edge deployments even during a major network outage or ransomware infection. Plus, Nodegrid’s ability to host Guest OS, including Docker containers and VNFs, allows companies to consolidate an entire edge networking stack in a single platform. Nodegrid devices like the