When Every Branch Matters: How a Credit Union Reinforced Network Resilience
When Every Branch Matters: How a Credit Union Reinforced Network Resilience
For many credit unions, digital transformation has expanded well beyond core banking systems. They depend on resilient IT infrastructure for everything from interactive teller machines, to cloud-hosted apps and remote employee access. But for their IT teams, this brings a growing list of challenges: more branches, more network equipment, and more pressure to minimize downtime. And often, they need to solve these challenges without adding staff.
That’s where the cracks begin to show.
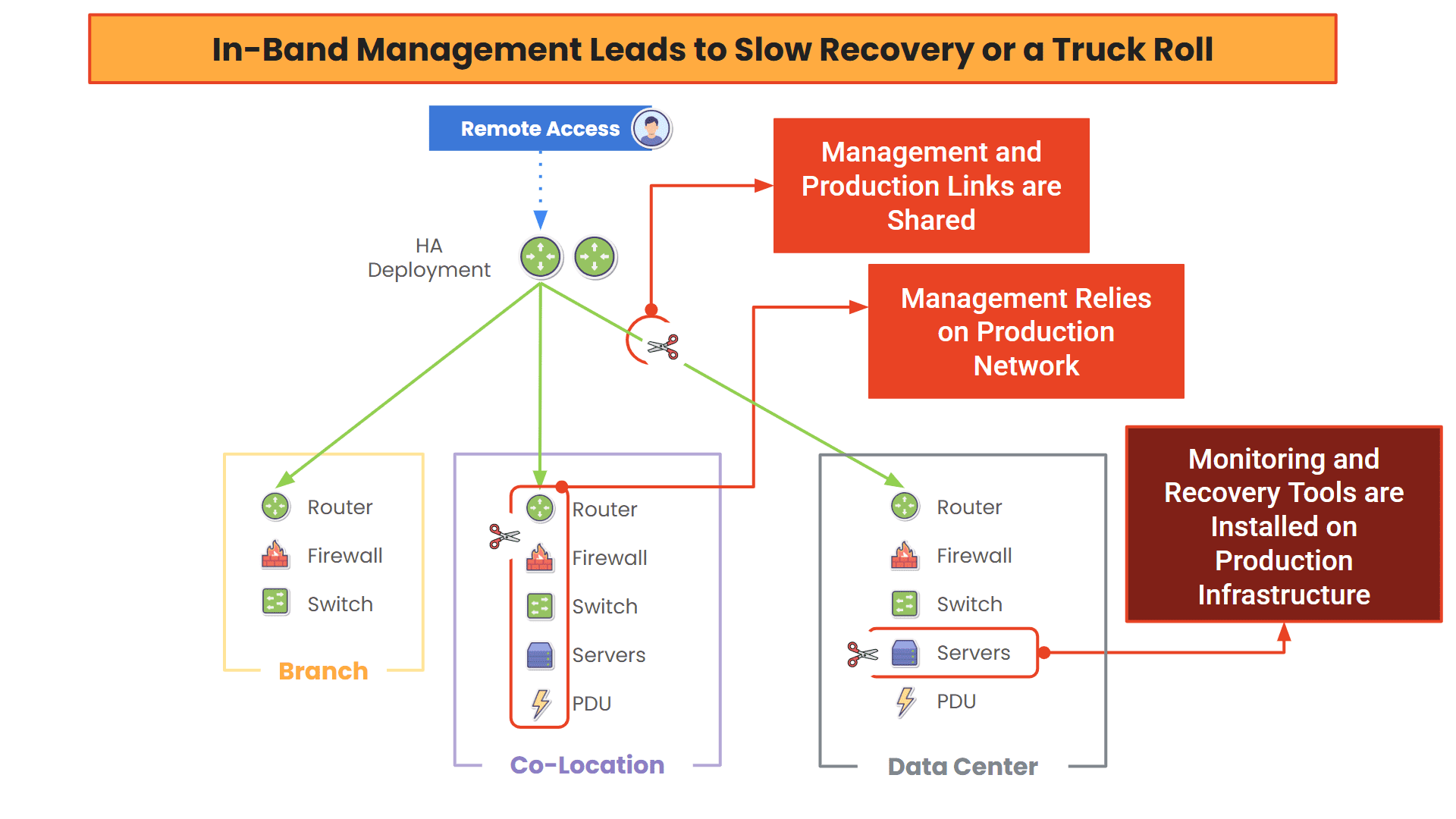
One mid-sized U.S. credit union faced a similar dilemma. They had to support more than 200 branch locations, but with only two IT staff. Routine network issues meant spending hours in the car, sometimes just to power cycle a device. Troubleshooting tasks or regular firmware updates easily consumed entire workdays. Combating outages was even worse because they lacked a reliable management path outside of the primary network. Long outages meant long workdays and lots of stress, not to mention the customer-facing issues like lost trust and reputation damage.
But instead of patching the problem, they made a bold move.
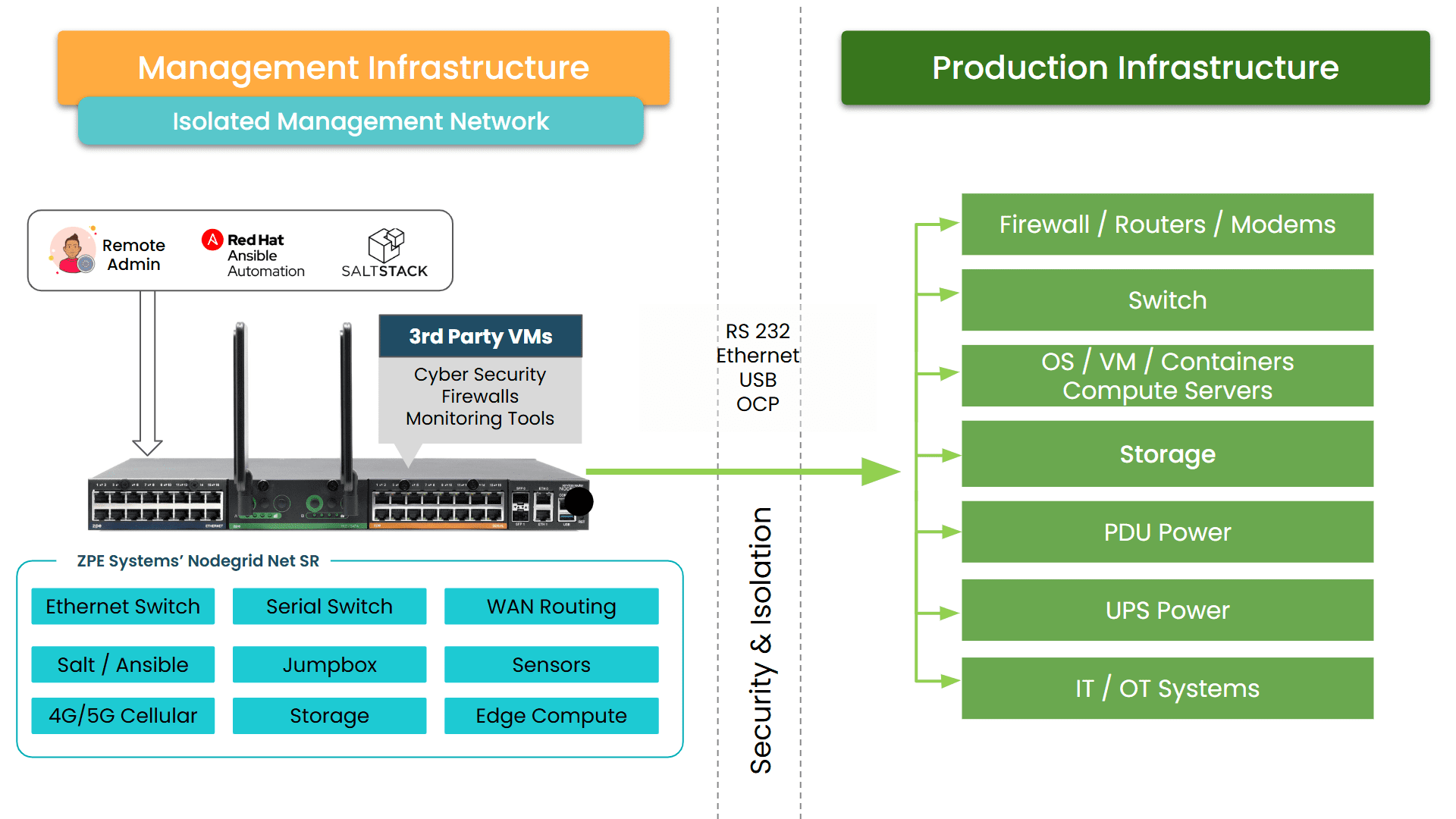
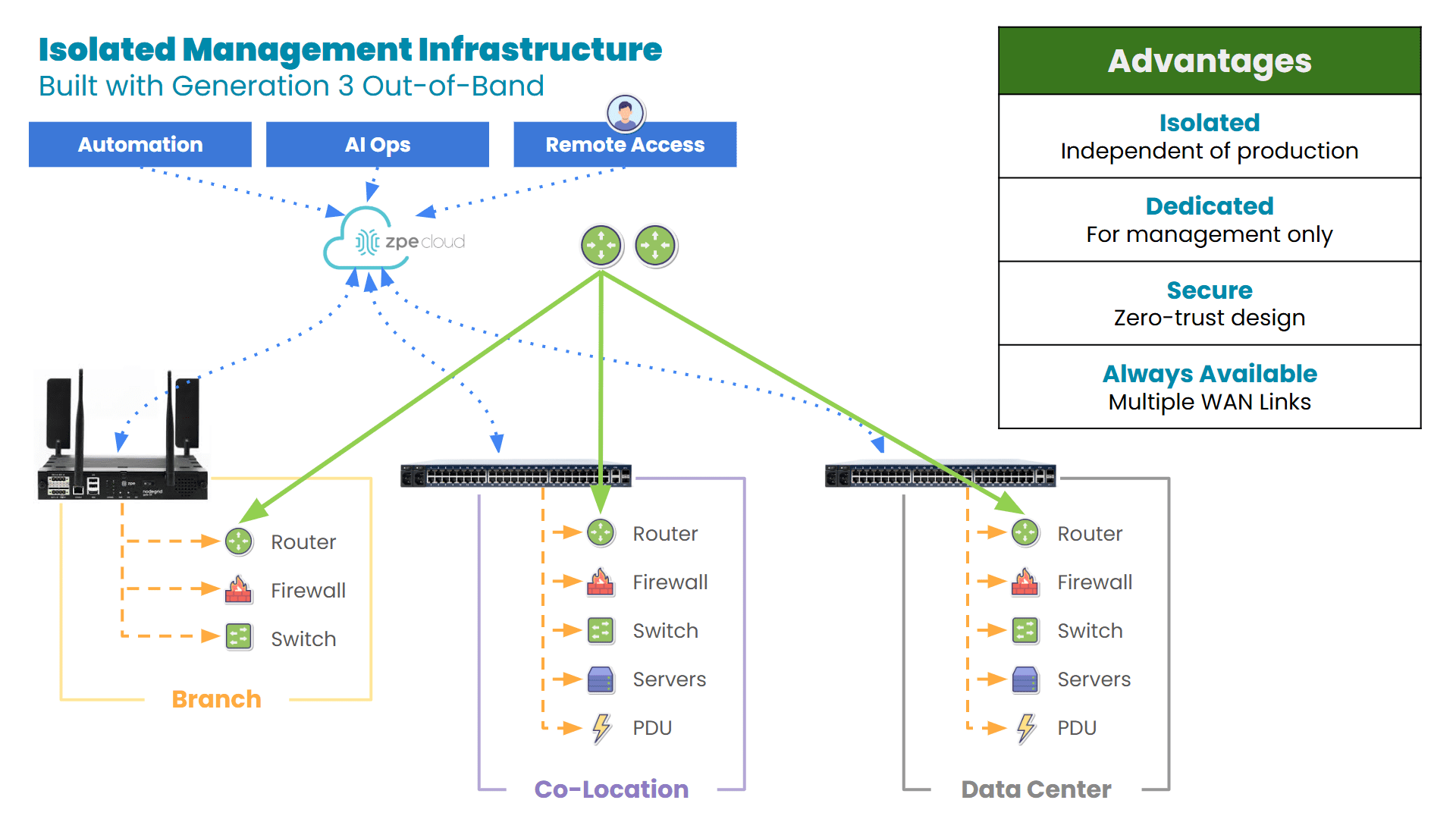
They adopted Nodegrid and ZPE Cloud, the out-of-band management solution that enables complete visibility and control, even when the main network fails. For the credit union’s IT team, this enabled them to perform all their jobs – from provisioning to troubleshooting, to device reboots – via remote session. The results? Drastically reduced travel costs, faster incident response times, and peace of mind knowing that every branch was protected by a resilient management backbone.
Download the full case study to see how they transformed their branch operations and set the foundation for secure, scalable growth.