Breaking Down The 2023 Ragnar Locker Cyberattacks

This article was written by James Cabe, CISSP, a 30-year cybersecurity expert who’s helped major companies including Microsoft and Fortinet.
Throughout 2023, several organizations were successfully hit by Ragnar Locker cyberattacks. The affected victims spanned the globe and were forced to shut down much of their critical operations, while the attackers demanded tens of millions of dollars in ransom payments. Despite the group being taken down by law enforcement in October, organizations are re-evaluating their defensive measures — and more importantly, their recovery strategies — to combat these attacks.
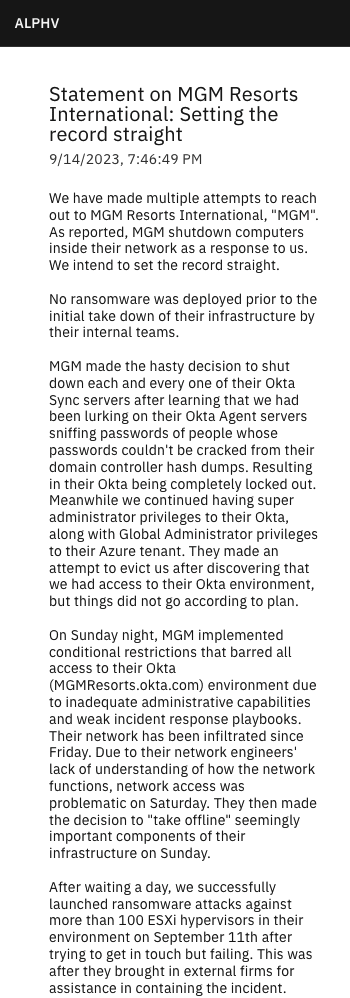
If you read my previous articles about the ongoing MOVEit breach and the ransomware that hit MGM, you probably know that isolation is key. It helps you fight through attacks by cutting the kill chain, so that you can restore services quickly without reinfection.
Who Carries Out Ragnar Locker Cyberattacks?
Recent Ragnar Locker cyberattacks were carried out by the Dark Angels Team cybercriminal group. Dark Angels Team’s modus operandi is to breach a company’s defenses, spread laterally, and steal data that can be used to extort the target company. The approach they take involves gaining access to the Windows domain controller, where they deploy ransomware. They encrypt devices using Windows and ESXi encryptors, which gives organizations little recourse aside from taking their critical systems offline in order to stop the spread.

How Do Ragnar Locker Cyberattacks Start?
Ragnar Locker breaches, like all ransomware attacks, require a kill chain that must first be initiated. MITRE ATT&CK defines this as the ‘initial,’ and in these attacks, the initial comes from social engineering. Email stuffing is often the tactic of choice, whereby the attacker sends an email that appears to have a trail of replies or forwards (see the example below). Email trails like this trick spam filters and land directly in the target’s inbox. When an employee clicks a malicious link inside the email, the attack kicks off.
Image: Email stuffing is used by marketers and threat actors alike to bypass spam filters.
How Do Companies Discover Ragnar Locker Cyberattacks?
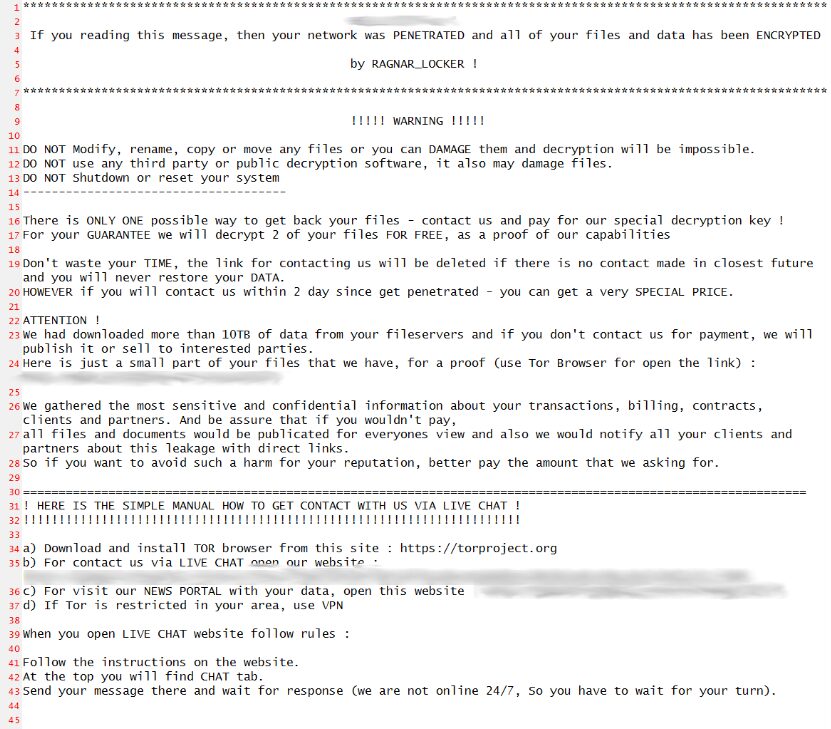
After the Ragnar Locker cyberattack kicks off, the bad link uses Java to load the locker ransomware, then a series of batch scripts installs a payload consisting of virtual box emulation software. This emulation software takes over and encrypts the host, and displays the ransomware message (see image below).
Image: A Ragnar Locker ransomware message showing on encrypted devices.
How Do Ragnar Locker Cyberattacks Spread?
The attack spreads by gaining access to Windows domain controllers and then attacking the management interfaces of the VMware ESXi machines. Most organizations don’t properly segment or isolate these management interfaces. This makes them especially vulnerable even to older Babuk ransomware source code that is an ESXi encryptor. Basically, the attackers only need to gain access to the management network, and then they can attack the production network.
From Intel471: “VMware’s ESXi is called a ‘bare metal’ hypervisor because the underlying hardware on which it is installed doesn’t need an operating system. ESXi allows the hardware to be utilized for multiple virtual machines (VMs), which saves on hardware costs. ESXi is a fruitful target for attackers since it may be connected to several VMs and the storage for them. Security experts warn ransomware actors have built specific binaries to target these systems. Groups joining this trend include HelloKitty, Black Basta, Cheerscrypt and GwisinLocker.”
They continue, “Over the last few years, several vulnerabilities have been identified in ESXi, including CVE-2021-21974. The vulnerability is a heap overflow vulnerability within Open Service Location Protocol (OpenSLP), which is a network discovery tool. The vulnerability is remotely exploitable over port 427, and has a Common Vulnerability Scoring System Version 3.0 (CVSSv3) base score of 8.8. It’s suspected that it may be the vulnerability exploited in this attack. VMware said that “significantly out-of-date products” were targeted with vulnerabilities that had been addressed. It affects ESXi versions 7.0 before ESXi70U1c-17325551, 6.7 before ESXi670-202102401-SG and 6.5 before ESXi650-202102101-SG. Due to other vulnerabilities in OpenSLP, VMware disabled OpenSLP starting in 2021 in ESXi versions 7.0 U2c and ESXi 8.0, which is the current version.”
Ultimately, these attacks exploit a combination of a lack of management plane isolation to the VMware management interfaces, specifically on port 427 (OpenSLP), and a lack of patching and updating. Organizations also typically lack a backup authentication mechanism for the control plane, as well as Privileged Access Management, which are both good fallback options.
How Can Companies Stop Ragnar Locker Cyberattacks?
Ragnar Locker ransomware and other attacks are successful because companies don’t employ proper management plane isolation. Attackers can gain access to VMware management interfaces, and then they essentially have the keys to the kingdom. That’s it. No amount of defense can save you.
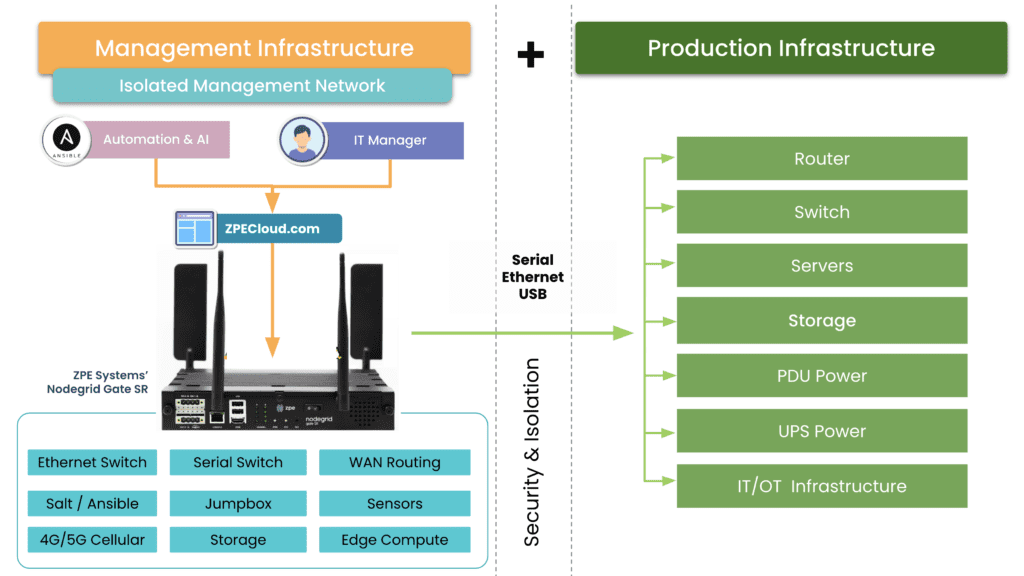
If you recall CISA’s binding operational directive, they call for an isolated management infrastructure. This is what we refer to as IMI. Rather than serving as a defense, like we think of traditional cybersecurity products, the IMI is an architecture that allows you to fight back. It’s your quick-reaction force, your cavalry, your secret weapon that ensures you always have a counterattack ready to deploy.
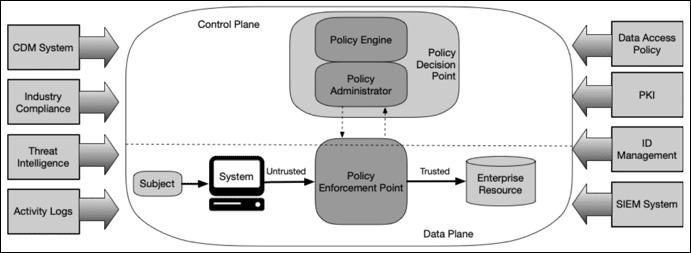
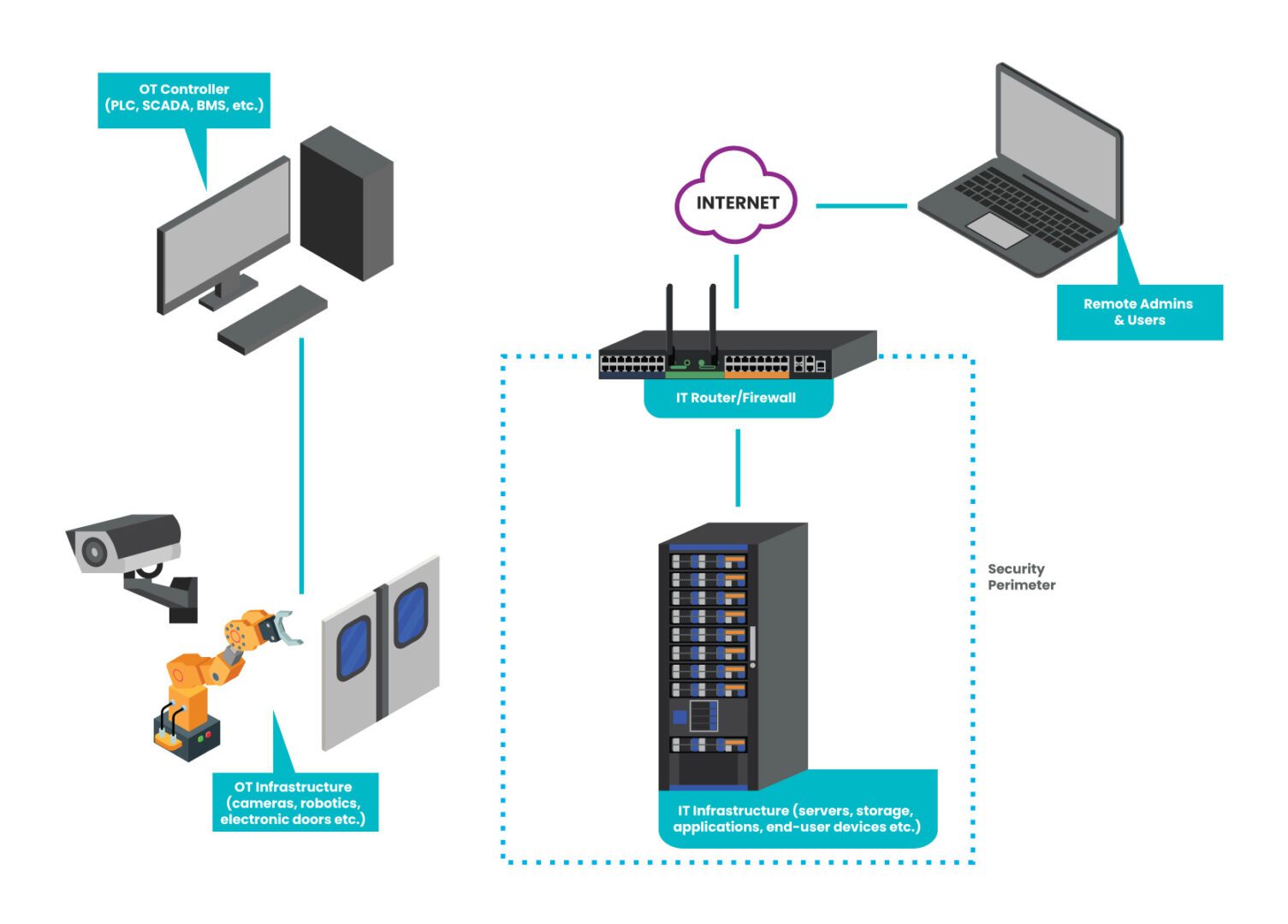
IMI is infrastructure that is dedicated — and most importantly, fully isolated from production assets — to ensuring operations can recover quickly from breaches and outages. Here’s a graphical breakdown:
The IMI includes all of the tools you need for rerouting traffic, decommissioning affected gear, wiping/re-imaging devices, and restoring infrastructure. You can also incorporate automation to speed the process along and make recovery something that happens in minutes or hours at the most. Aside from being completely isolated from production assets, the IMI itself is also segmented and employs zero trust practices. This means that you and only you have access to your secret weapon for cutting the ransomware kill chain.
How Do You Use Isolated Management Infrastructure?
An IMI can host an IRE (Isolated Recovery Environment), which is used to cut off all user data and remote access (except for OOB) to an entire infected site. A properly implemented recovery environment should automate most of these activities to speed up the recovery. One of the first considerations is the requirement for a secondary organization in your IAM that is not attached to normal operations. This is what is known as a set of “Break the Glass” accounts. These are known in military circles but have made it into formal practice as part of a strong playbook for ransomware. Once you do this, you can instantiate selected Zero Trust remote access to the site using credentials that are not in the scope of the attack, and then bring up a communications channel for a virtual war room using software like Rocket Chat, Jitsi, Slack, or other standalone communications tools that are installable on the IRE environment.
Avoiding normal authentication methods or IAM and normal communication channels is required for the integrity of the recovery and strengthens the recovery playbook. During this time, no email may be used that is associated directly with the organization. Ideally, email should never touch an account that is associated with it either.
The next step is to create a new set of clean side networks that do not directly connect to the main backbone or put it behind another firewall for triage good/bad. Using a sniffer software running on the IRE, the recovery team can then run a passive scan or an active scanner against all machines continuing to try to send email to Exchange/M365. You can give access to people that are deemed good (not sending traffic) but lock off (with an EDR) the ability to open Outlook for a while, while keeping them on the web email. From there, continue working through to find all the sending drivers to see if they have a good backup. If not, back up the infected drive for offline data retrieval for later. Then re-image while scanning the UEFI BIOS during boot (if needed, run an IPMI scan). If the site has a list of assets that are considered crown jewels, prioritize these.
Once you have a segmented “clean side” established with all the network services required to operate the site (DNS, IAM, DHCP), then Internet access can be restored to this site on a limited basis; which means only out-bound communications, nothing in-bound. Restorative operations can continue apace. making sure that the infected side assets are captured in backup for later forensics following chain-of-custody if damages exceeding insurance limits are found to be the case. This is decided in the war room.
Download the Isolated Management Infrastructure Blueprint
Now is the time to lay the groundwork for your IMI so you can fight back against ransomware. Download the Network Automation Blueprint, which gives you a step-by-step guide to building your Isolated Management Infrastructure.
Get in touch with me!
True security can only be achieved through resilience, and that’s my mission. If you want help shoring up your defenses, building an IMI, and implementing a Resilience System, get in touch with me. Here are links to my social media accounts: