ISPs: What Happens When You Can’t Reach the Console?
Imagine the scenario from our last article: It’s 2am, a core router just went down, and customers in three regions have your phone ringing off the hook. You try SSH. No response. You ping through the management VLAN. Again, nothing.
What about the console port? This is your last lifeline to see what’s happening under the hood. But when you can’t reach it remotely, recovery slows to a crawl. What should have been a quick fix is now turning into hours of downtime, unhappy customers, and potential SLA penalties.
Things can really spiral out of control for ISPs who depend on their production networks for management. Let’s look at the biggest technical hurdles and business impacts that crop up, and the approach ISPs are taking to make sure they’re always in control.
The Problems When Console Access Is Gone
1. Recovery Turns Into a Road Trip
Technical hurdle: No console access means your only option is to dispatch engineers to the site, plug in manually, and perform recovery by hand.
Business impact: Each truck roll burns thousands of dollars, drags engineers away from other projects, and extends downtime. Customers lose trust and SLA penalties are suddenly on the table.
2. Small Outages Turn Into Big Problems
Technical hurdle: A single misconfigured update or failed device can have a snowball effect when you don’t have console visibility. You can’t isolate the fault quickly, and the blast radius grows.
Business impact: What could have been a quick local fix becomes a regional outage that puts business networks and enterprise accounts at risk.
3. Security and Compliance Take a Back Seat
Technical hurdle: In an emergency, teams know that they have to fix the problem fast. This means they’re likely to cut corners exposing management ports to the internet or using outdated console servers that have weak security.
Business impact: These shortcuts open the door to ransomware and compliance failures that could cost much more than the immediate outage.
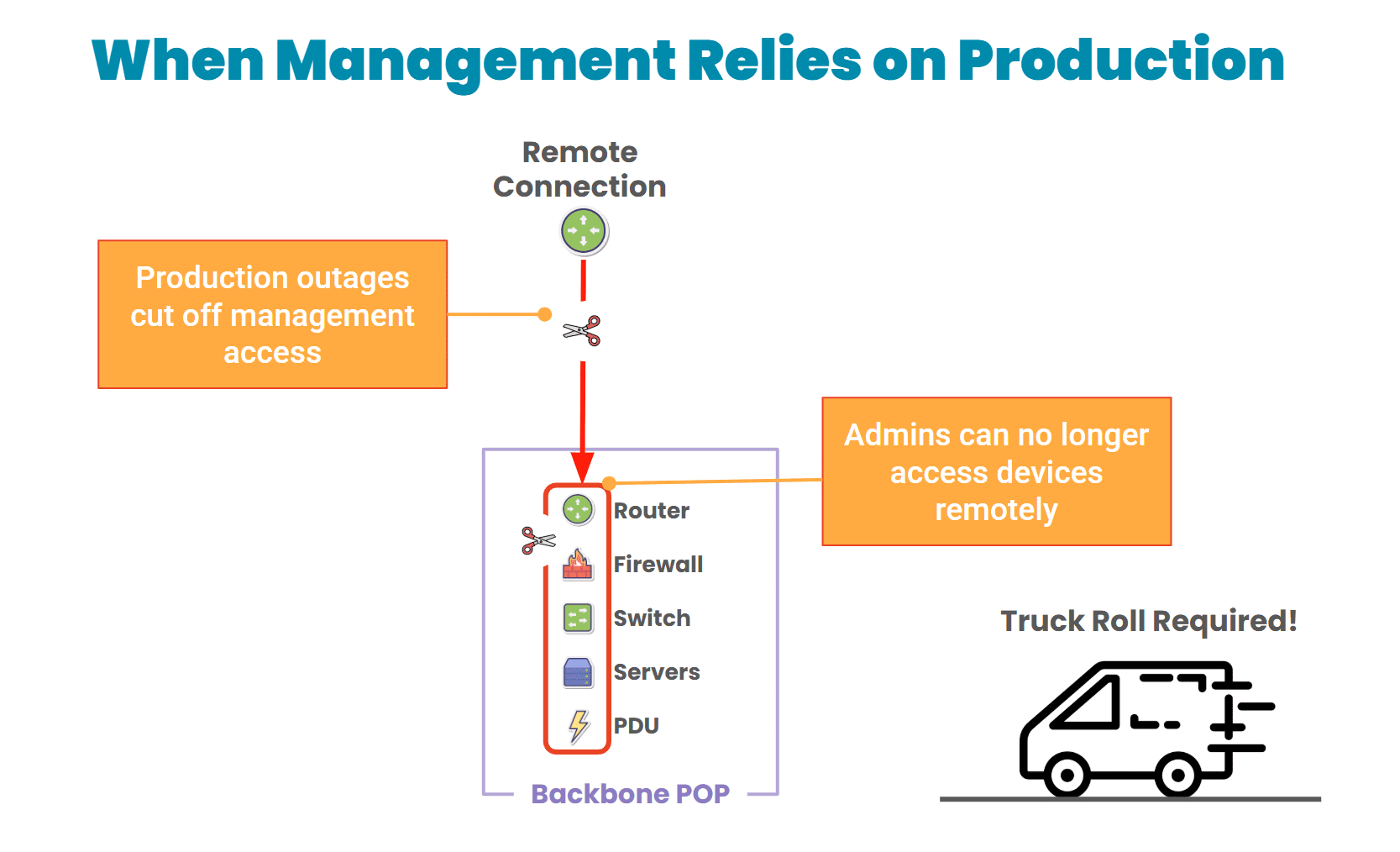
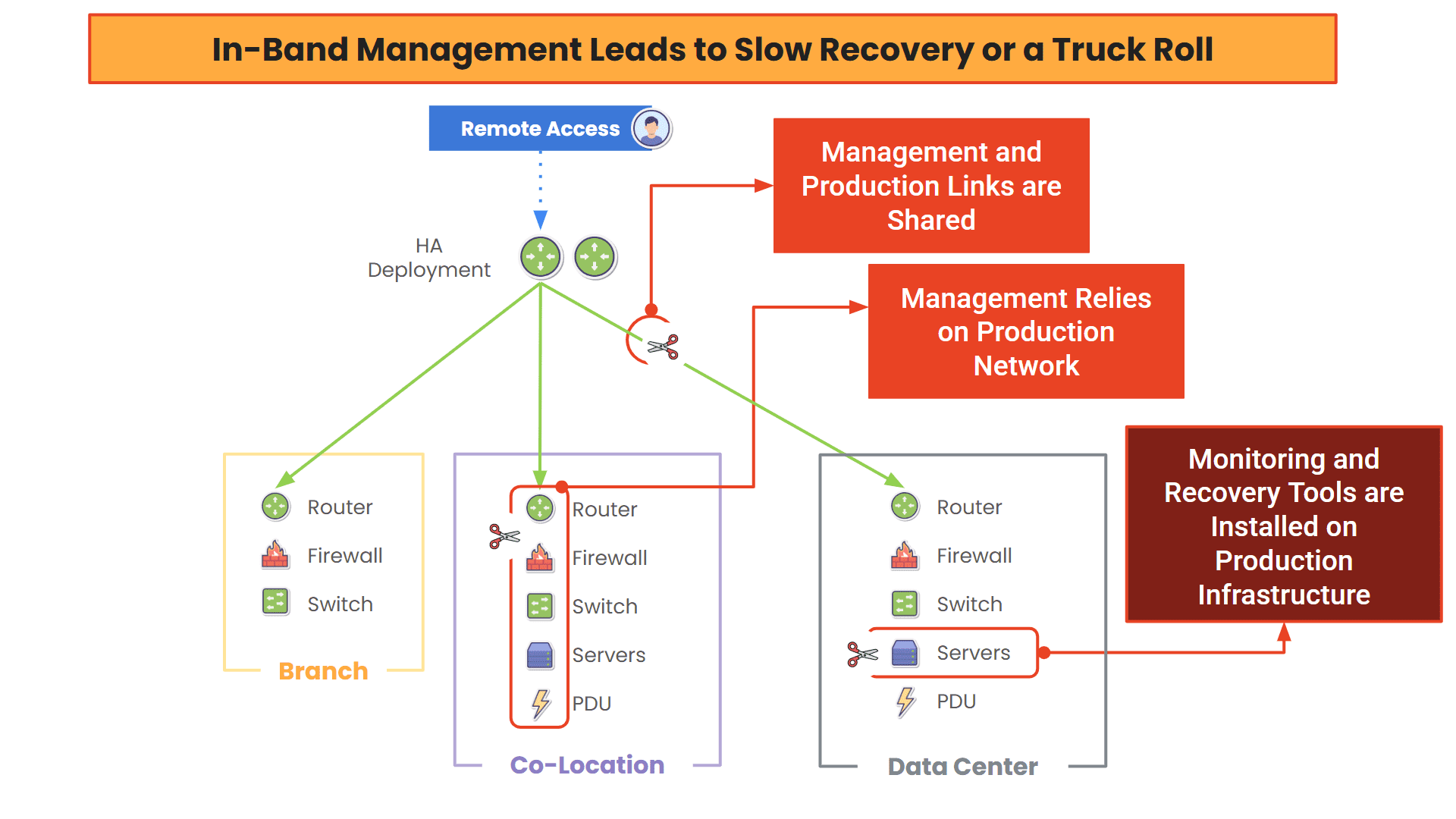
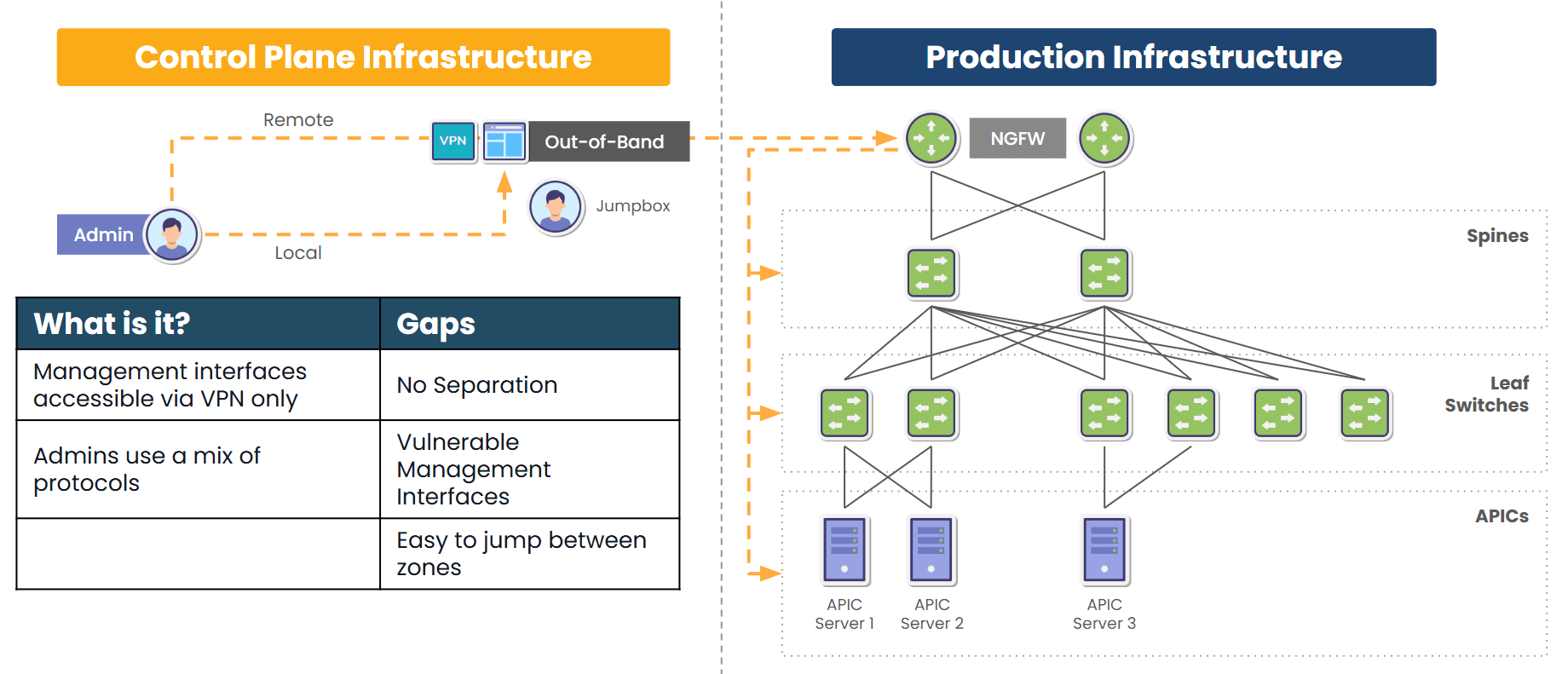
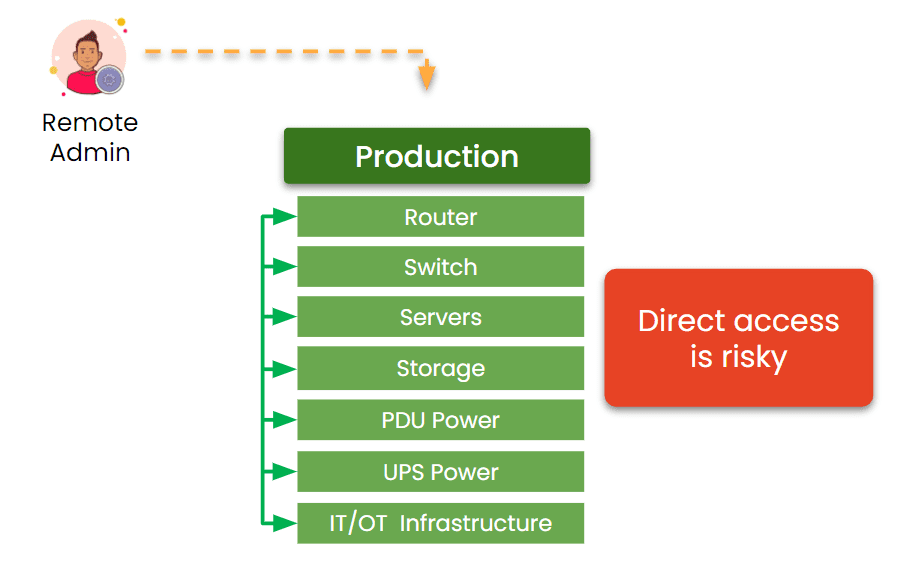
Diagram: When management access depends on the production network, teams can’t recover from outages without going on-site to manually restore services.
The Technical Fix: Out-of-Band & IMI
It’s common to route management traffic through production networks. But this creates a “shared fate” problem: when production goes down, management goes with it.
ZPE Systems created the best practices that are used today and now recommended by CISA, the NSA, and the FBI. Here are the two critical components that fix the “shared fate” problem:
- Out-of-Band: Provides alternate connectivity (5G, satellite, secondary fiber) so you always have a way to connect to your devices, even if they’re thousands of miles away.
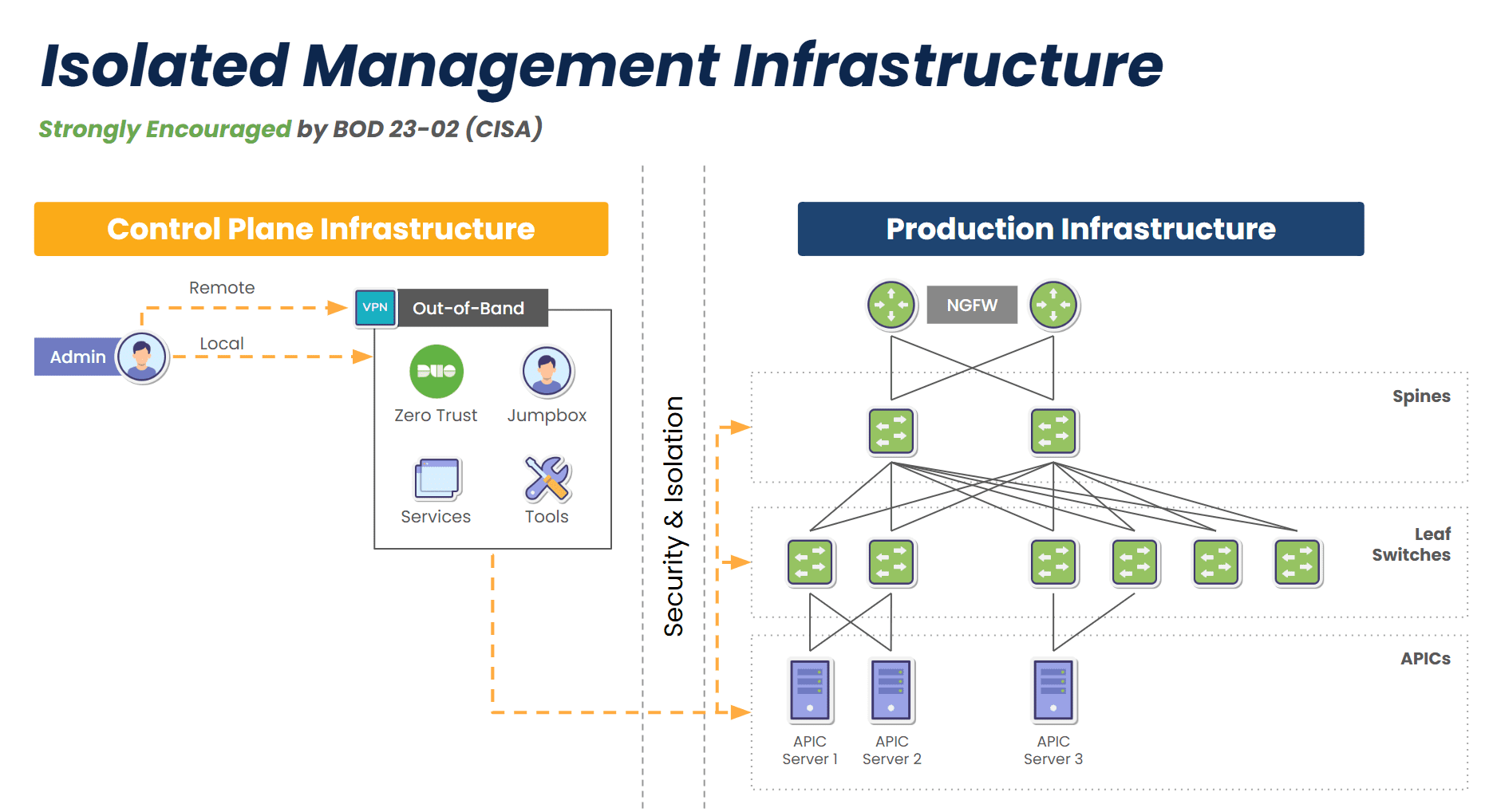
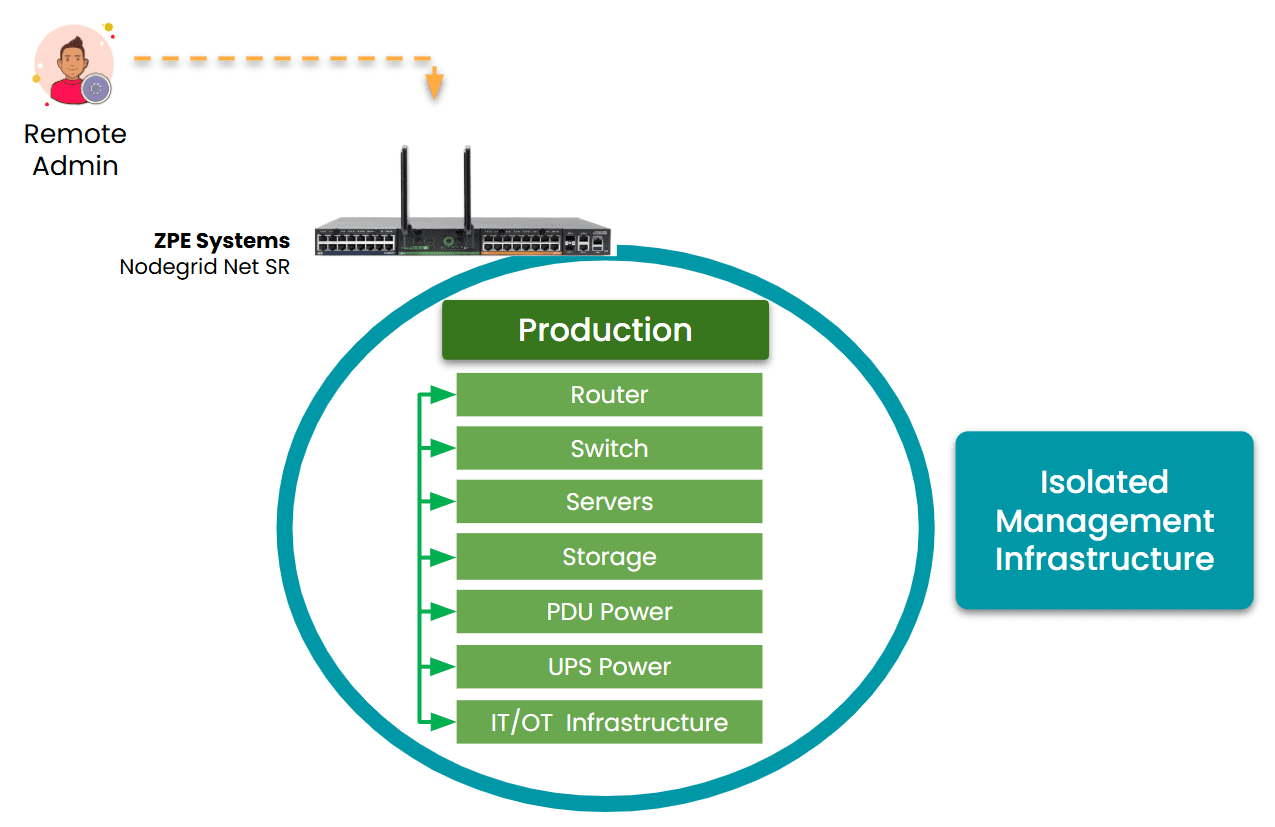
- Isolated Management Infrastructure: Physically and logically separates management from production, enforcing zero trust controls to keep attackers out, limit lateral movement, and accelerate ransomware recovery.
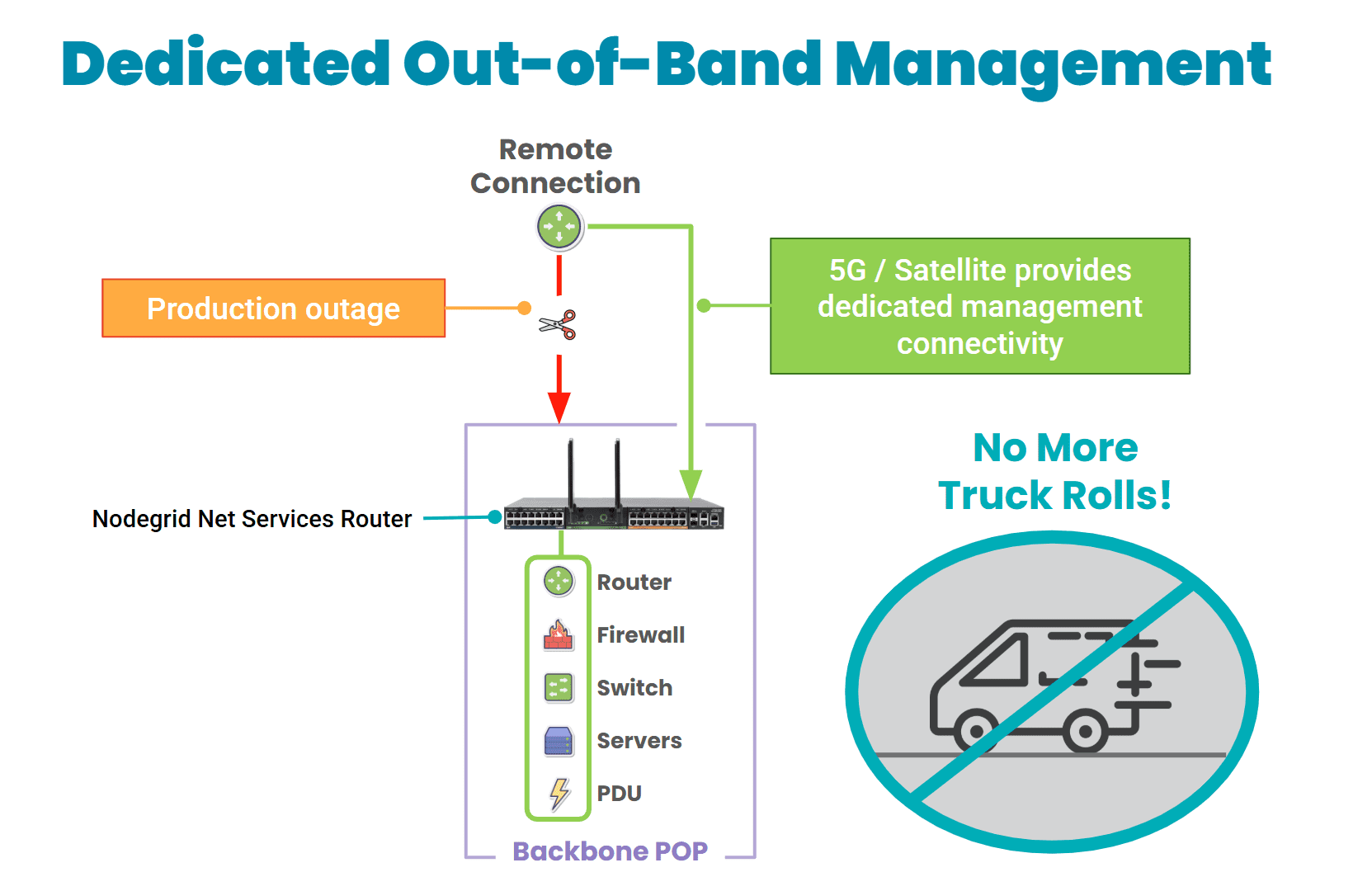
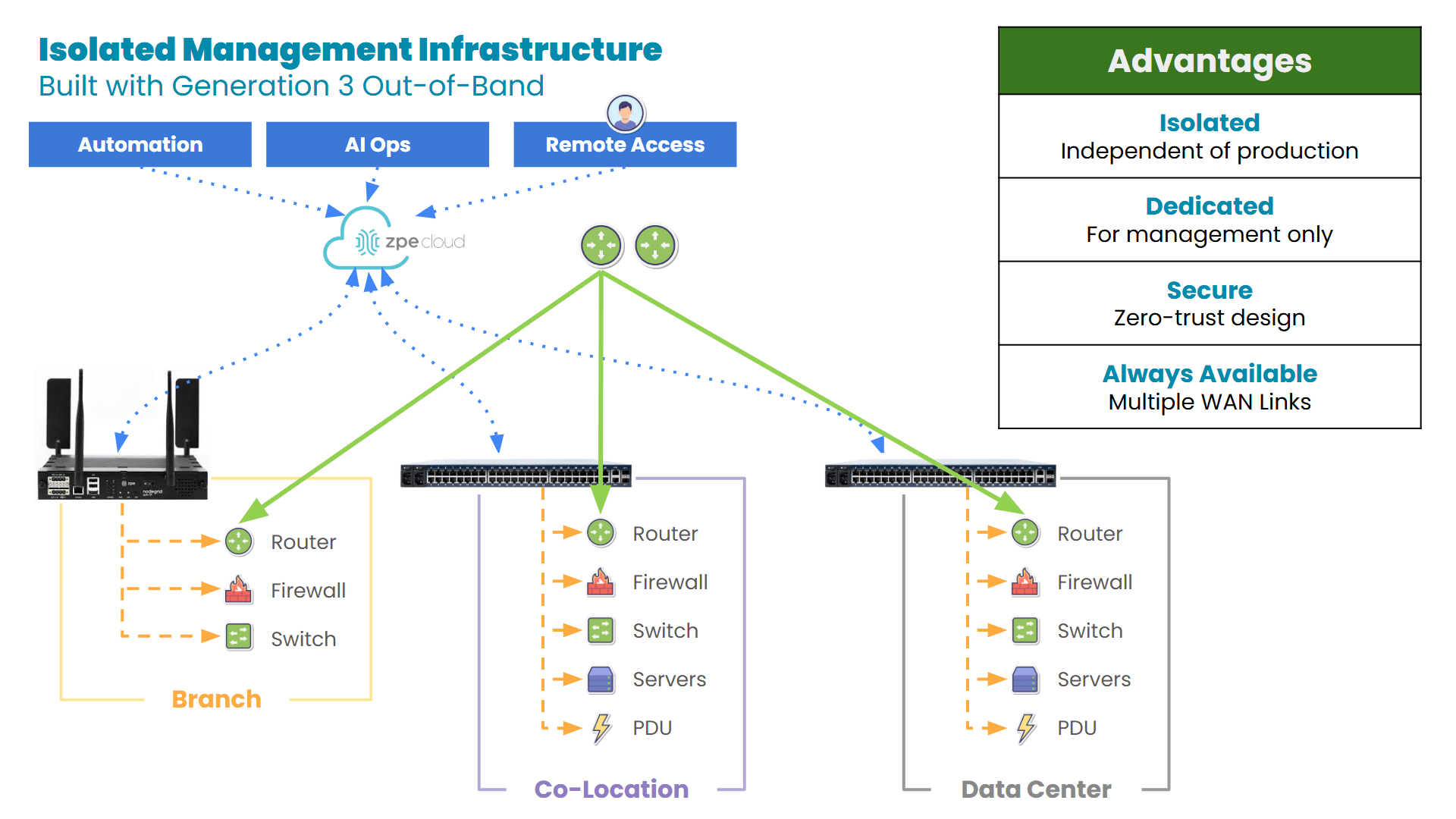
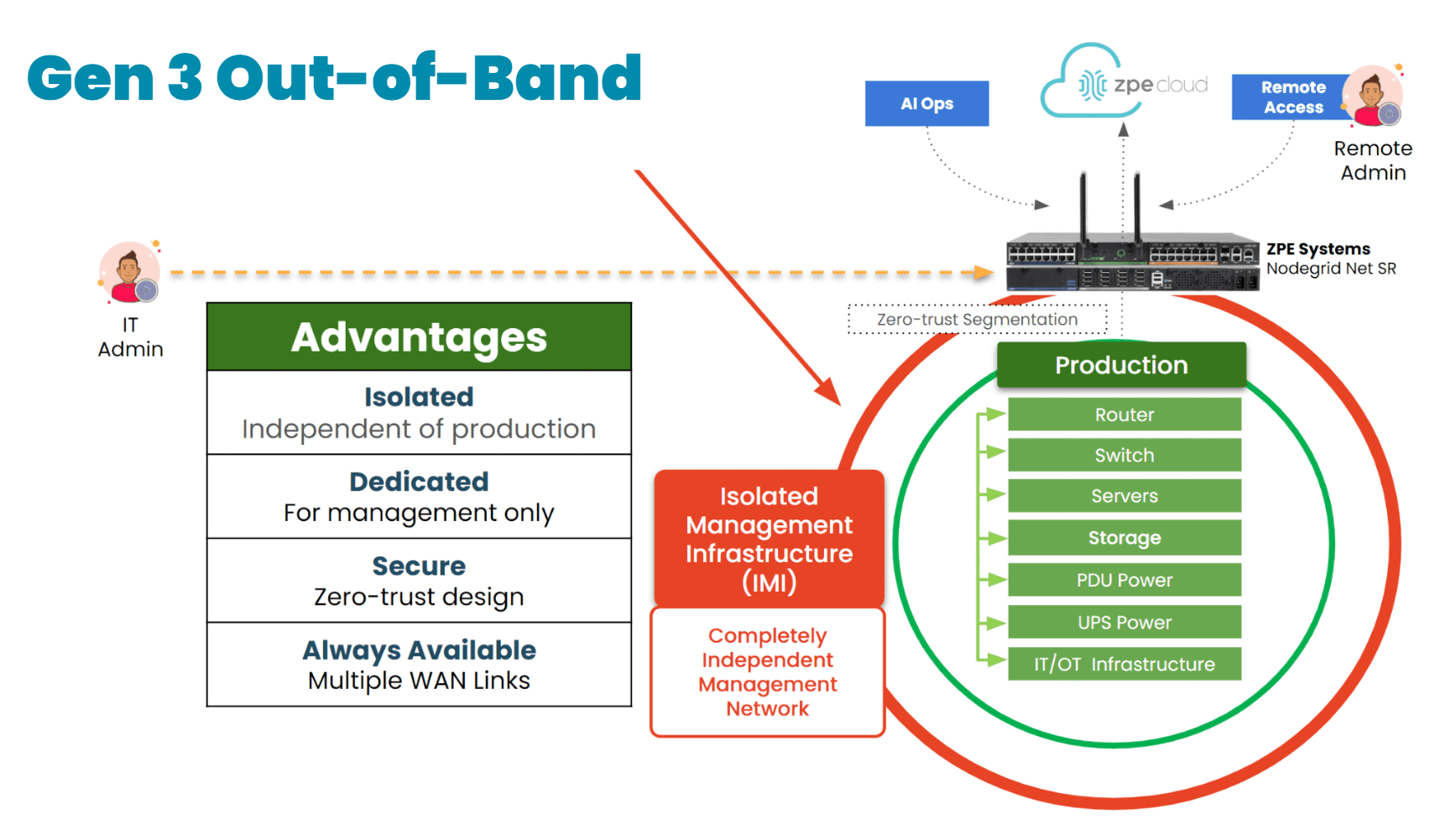
Diagram: Out-of-band provides a fully isolated management infrastructure with dedicated 5G, satellite, and other links that ensure remote access even when production networks go offline.
OOB and IMI ensure management access is always on, always secure, and always independent. Instead of rolling a truck and waiting hours for services to be restored, you can use your dedicated out-of-band path to instantly access sites from your browser. Nodegrid gives you complete, low-level remote control of devices as if you’re physically connected, so you can recover in minutes. This is critical for ISPs.
Why ZPE Systems’ Nodegrid Is Ideal for ISPs
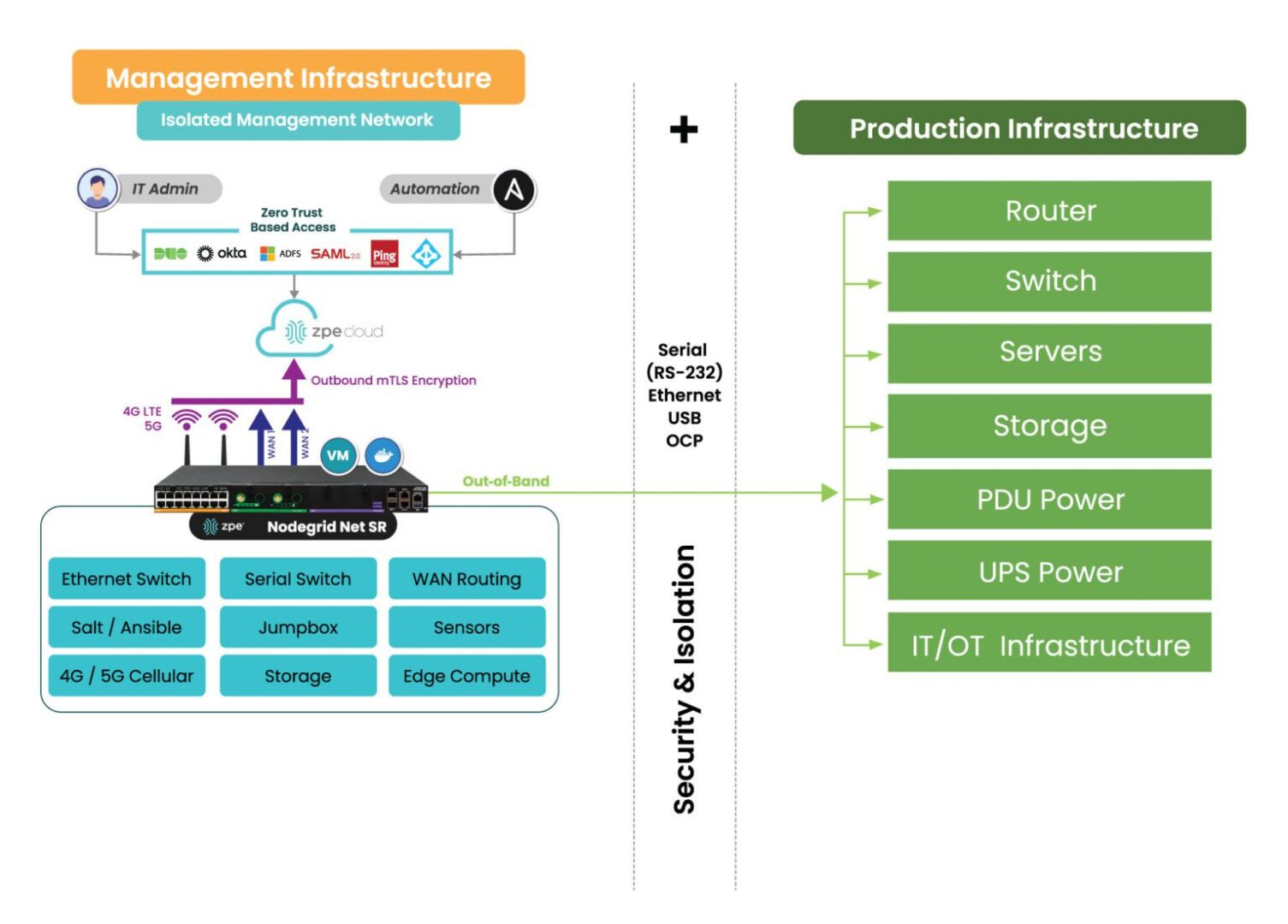
Nodegrid is built specifically to give ISPs resilient, secure, and scalable management by combining all the functions of OOB and IMI into one device. This pairs with ZPE Cloud or on-prem Nodegrid Manager to give ISPs full remote access, visibility, and control of their distributed sites.
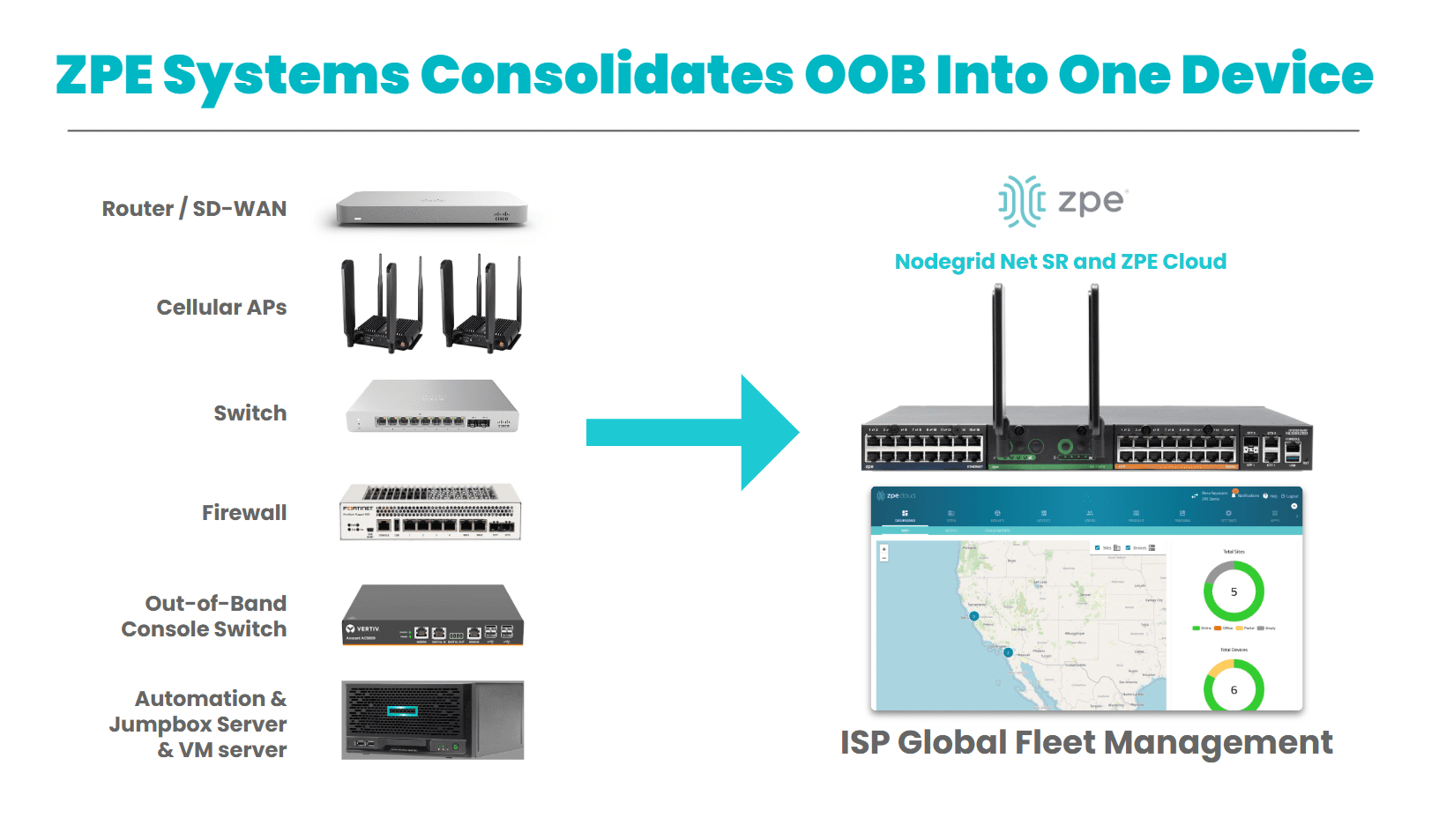
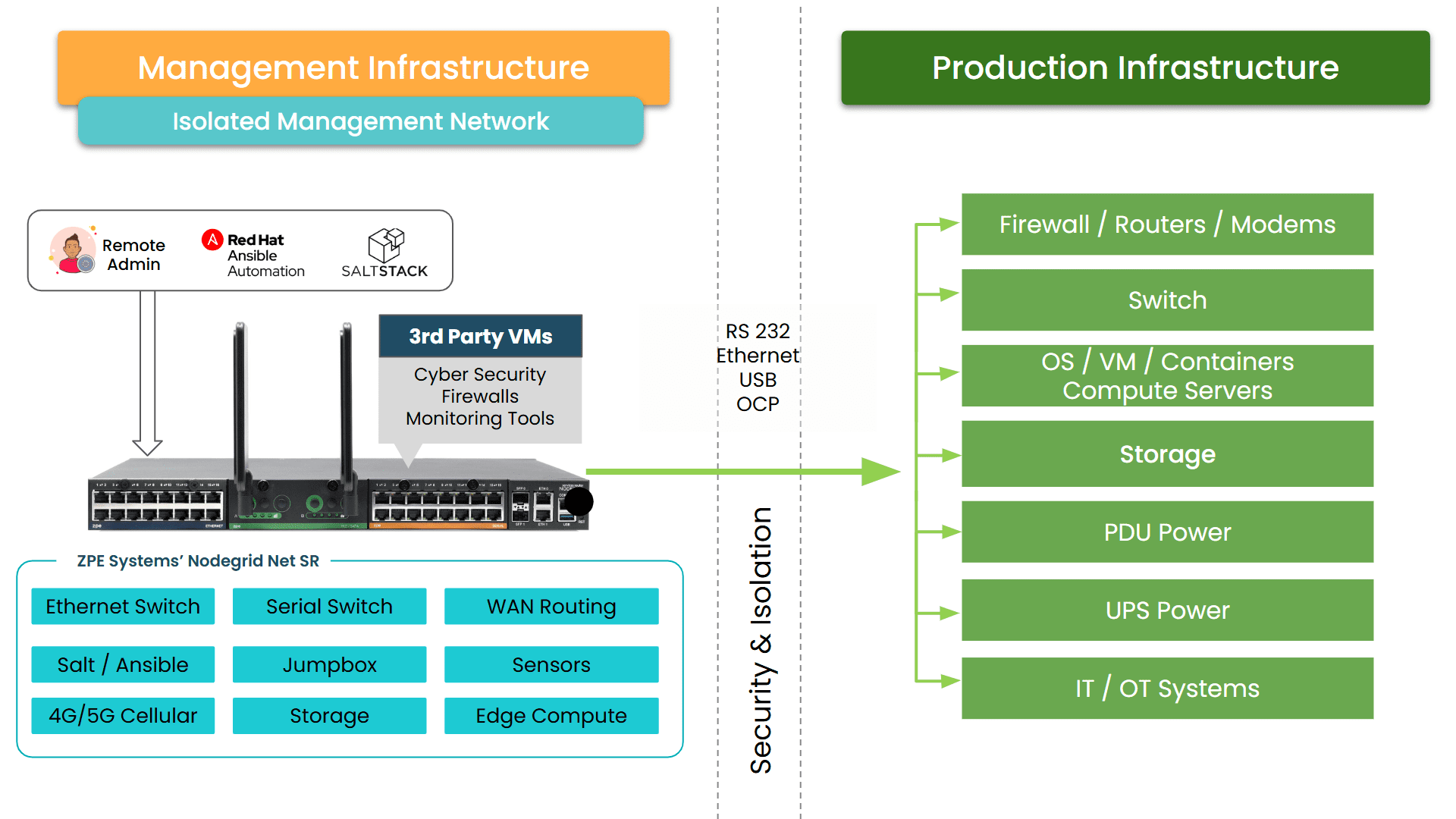
Image: ZPE Systems’ Nodegrid devices consolidate more than six management functions into one device, and pair with ZPE Cloud or Nodegrid Manager for holistic remote control of ISP fleets.
Whether you’re a Tier 1 operating backbone POPs, or a Tier 3 keeping local last-mile hubs online, Nodegrid gives you benefits including:
- Always-on console access via 5G/LTE, Starlink, or secondary fiber.
- Zero trust enforcement with RBAC, MFA, and continuous verification.
- FIPS 140-3 certified encryption for airtight security.
- Centralized policy control with ZPE Cloud or on-prem Nodegrid Manager.
- Device consolidation: console server, LTE modem, Ethernet switch, and security gateway in one appliance.
More ISPs are realizing these benefits and switching to Nodegrid using an approach that doesn’t require them to disrupt services. Take the Internet Association of Australia, for example. They were able to perform a nationwide rollout of Nodegrid at 35 POPs while maintaining 100% uptime, removing 70 devices from the management stack, and saving $17,500/month in costs. Read the IAA case study for full details, including diagrams and photos.
Here’s How To Deploy Nodegrid With Zero Downtime
There’s a lot at stake when you can’t reach the console during a failure or outage. But Nodegrid helps you quickly resolve those 2AM wakeup calls with secure remote access to all your systems.
To help you, we put together this Zero-Downtime Migration Checklist. Download this guide to see every step — from assessing infrastructure needs, to designing the right solution and validating after migration — and how you can deploy the most resilient ISP network management solution.