Automated PDU Provisioning and Configuration
Summary
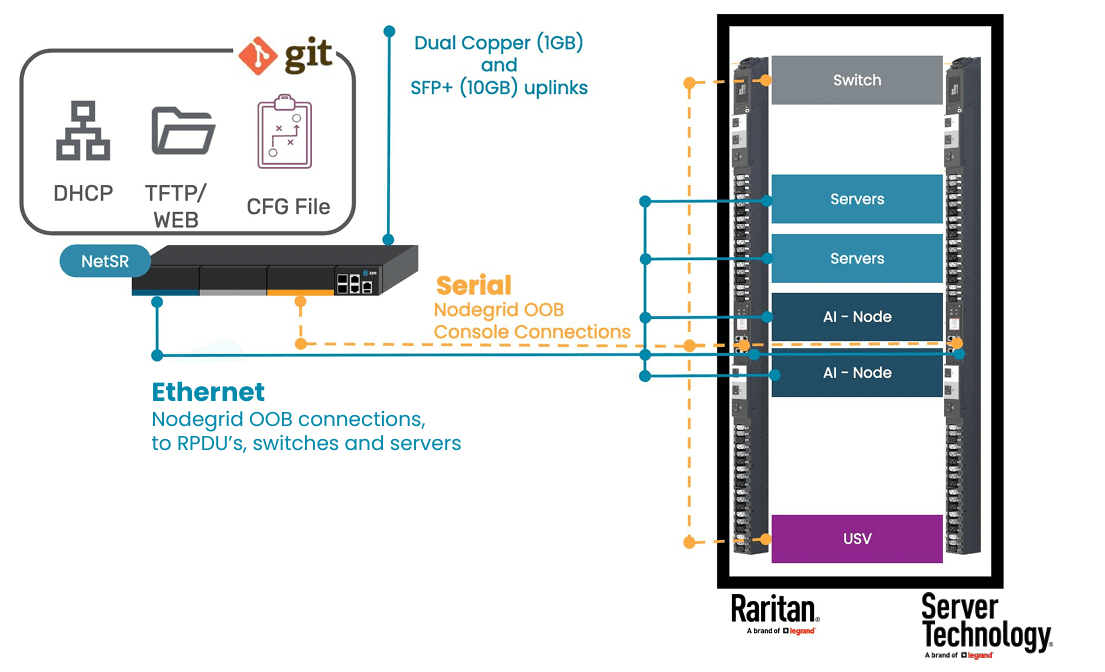
Rack Power Distribution Units (RPDUs) are critical to data center infrastructure. These ensure adequate power is distributed to all servers, storage, networking, and other equipment. Much like this equipment, however, RPDUs must be configured and maintained; otherwise, outages can occur and affect the business’ bottom line.
The common practice for managing RPDUs involves manually configuring and performing frequent updates. This poses three challenges:
- Skilled engineers need to be on-site to perform configuration tasks
- RPDUs must be configured individually, which consumes valuable time
- Manually configuring RPDUs can introduce human errors that may lead to catastrophic failures or compliance issues
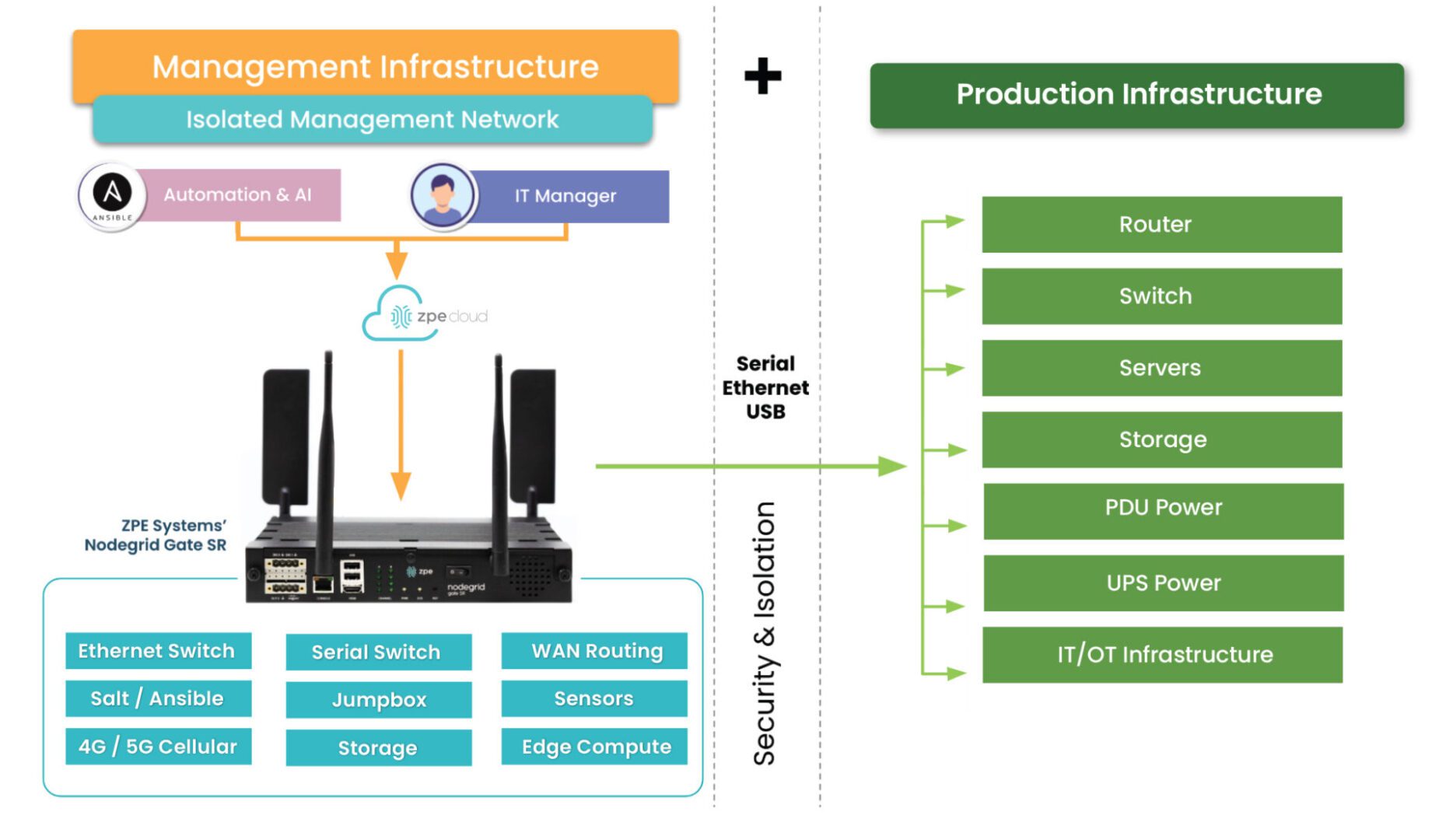
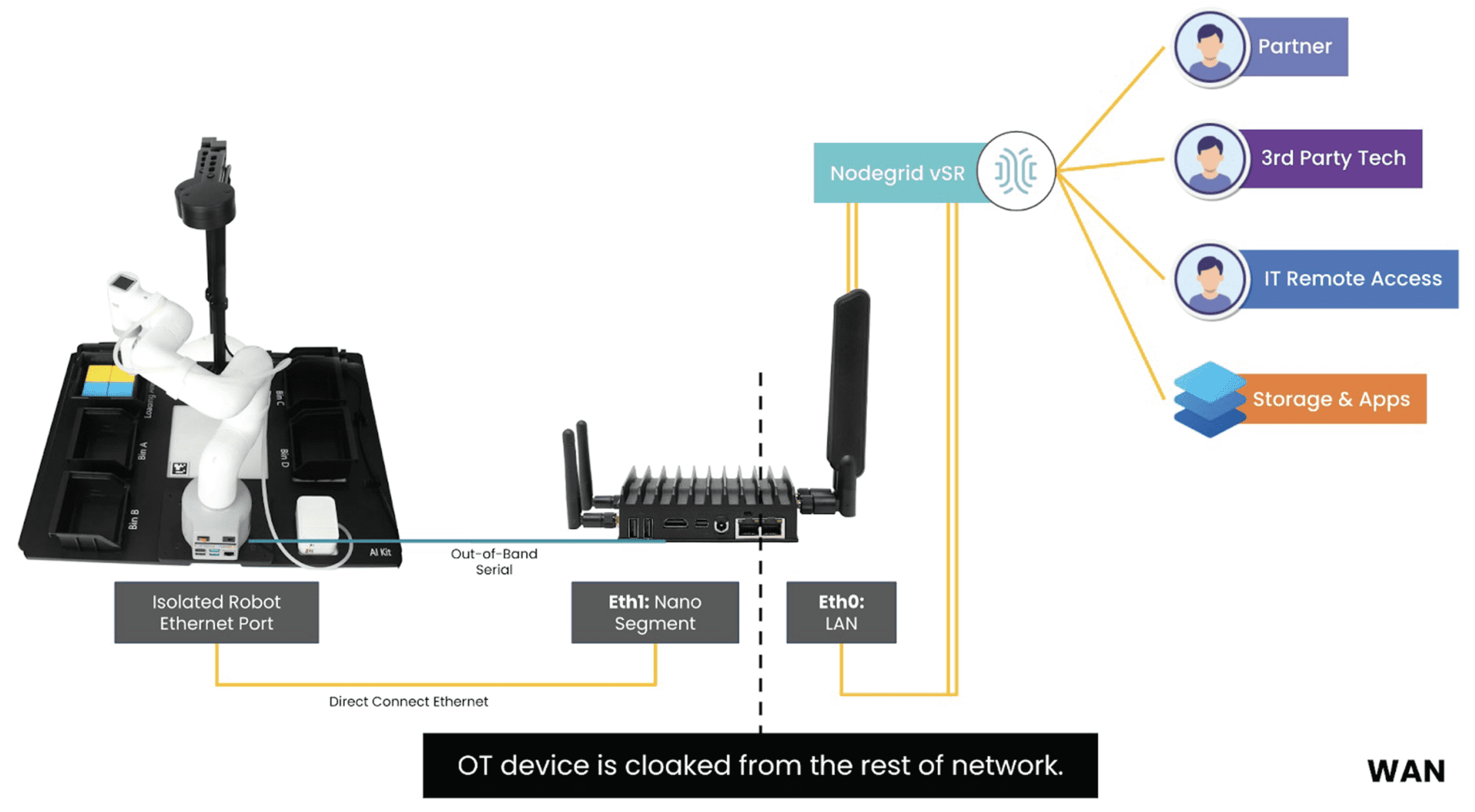
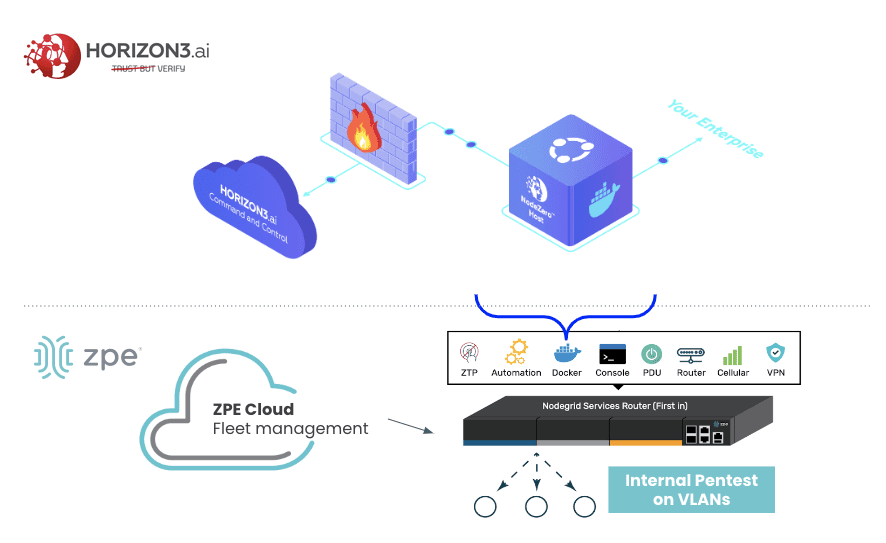
ZPE Systems solves these challenges with its Nodegrid platform. Nodegrid enables automated deployments and centralized management, which help IT teams configure multiple RPDUs simultaneously, reduce the risk of errors, and eliminate the need for extra networking equipment. These advantages save valuable time and money by allowing efficient, hands-off data center operations.
Download the RPDU solution guide below for full details about this solution, including a wiring diagram and a step-by-step outline of how to set it up.