NIS2 Compliance & Requirements

NIS2 – an update of the EU’s Network and Information Security Directive – seeks to enhance the cybersecurity level and resilience of EU member states. Compared to the original NIS, it significantly increases risk management, corporate accountability, business continuity, and reporting requirements. NIS2 became law in all EU member states on 17 October 2024, so affected organizations must take action to avoid fines and other penalties. This guide describes the 10 minimum cybersecurity requirements mandated by NIS2 and provides tips to simplify NIS2 compliance. Citation: Directive (EU) 2022/2555 of the European Parliament and of the Council of 14 December 2022 on measures for a high common level of cybersecurity across the Union, amending Regulation (EU) No 910/2014 and Directive (EU) 2018/1972, and repealing Directive (EU) 2016/1148 (NIS 2 Directive)
Who does NIS2 apply to, and what are the consequences for noncompliance?
NIS2 applies to organizations providing services deemed “essential” or “important” to the European economy and society. Essential Entities (EE) generally have at least 250 employees, annual turnover of €50 million, or balance sheets of €43 million. Essential sectors include:
- Energy
- Transport
- Finance
- Public administration
- Health
- Space
- Water supply (drinking & wastewater)
- Digital infrastructure (e.g., cloud computing providers)
Important Entities (IE) generally have at least 50 employees, annual turnover of €10 million, or balance sheets of €10 million. Important sectors include:
- Postal services
- Waste management
- Chemicals
- Research
- Food
- Manufacturing (e.g., medical devices and other equipment)
- Digital providers (e.g., social networks, online marketplaces)
The NIS2 Directive outlines three types of penalties for noncompliance: non-monetary remedies, administrative fines, and criminal sanctions. Non-monetary remedies include things like compliance orders, binding instructions, security audit orders, and customer threat notification orders. Financial penalties for Essential Entities max out at €10 million or 2% of the global annual revenue, whichever is higher; for Important Entities, the maximum is €7 million or 1.4% of the global annual revenue, whichever is higher. NIS2 also directs member states to hold top management personally responsible for gross negligence in a cybersecurity incident, which could involve:
- Ordering organizations to notify the public of compliance violations
- Publicly identifying the people and/or entities responsible for the violation
- Temporarily banning an individual from holding management positions (EEs only)
Even the nonfinancial penalties of NIS2 noncompliance can affect revenue by causing reputational damage and potential lost business, so it’s crucial for IEs and EEs to be prepared when this directive takes effect in their state.
10 Minimum requirements for NIS2 compliance
The NIS2 directive requires essential and important entities to take “appropriate and proportional” measures to manage security and resilience risks and minimize the impact of incidents. It mandates an “all-hazards approach,” which means creating a comprehensive business continuity framework that accounts for any potential disruptions, whether they be natural disasters, ransomware attacks, or anything in between. Organizations must implement “at least” the following requirements as a baseline for NIS2 compliance (click links for more info):
1. Risk analysis and information system security policies
Organizations must create and update comprehensive policies covering cybersecurity risk analysis and overall IT system security practices. These policies should cover all the topics listed below and include specific consequences and/or corrective measures for failing to follow the outlined processes.
| Tip: Keeping all company policies in a centralized, version-controlled repository will help track updates over time and prevent anyone from making unauthorized changes. |
2. Security incident handling
Entities must implement incident-handling tools and practices to help accelerate resolution and minimize the impact on end users and other essential or important services. This includes mechanisms for identifying problems, triaging according to severity, remediating issues, and notifying relevant parties. NIS2 outlines a specific timeline for reporting significant security incidents to the relevant authorities:
- Within 24 hours – Entities must provide an early warning indicating whether they suspect an unlawful or malicious attack or whether it could have a cross-border impact.
- Within 72 hours – Entities must update the relevant authorities with an assessment of the attack, including its severity, impact, and indicators of compromise.
- Within one month – Organisations must submit a final report including a detailed description of the incident, the most likely root cause or type of threat, what mitigation measures were taken, and, if applicable, the cross-border impact. If the incident is still ongoing, entities must submit an additional report within one month of resolution.
| Tip: AIOps (artificial intelligence for IT operations) analyzes monitoring logs using machine learning to identify threat indicators and other potential issues that less sophisticated tools might miss. It can also generate, triage, and assign incidents, perform root-cause analysis (RCA) and other automated troubleshooting, and take other actions to streamline security incident handling. |
3. Business continuity and crisis management
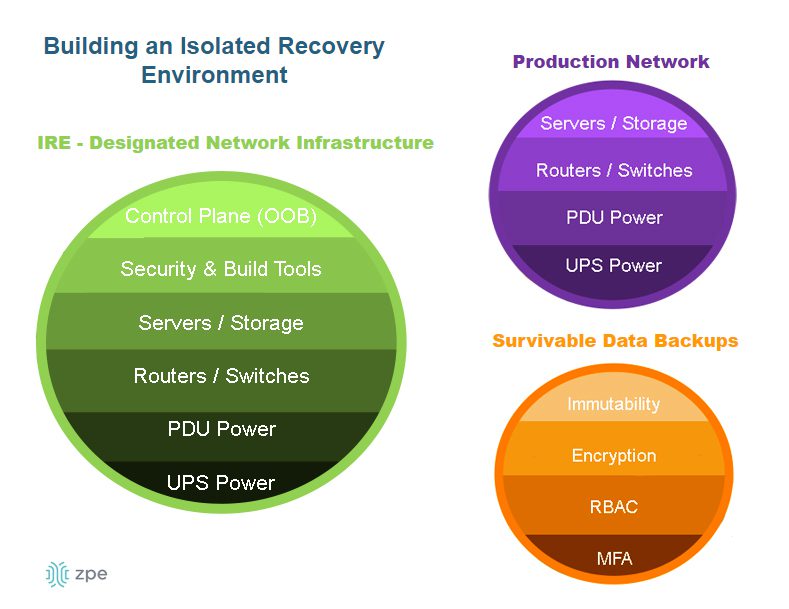
Essential and important entities must establish comprehensive business continuity and crisis management strategies to minimize service disruptions. These strategies should include redundancies and backups as part of a resilience system that can keep operations running, if in a degraded state, during major cybersecurity incidents. It’s also crucial to maintain continuous access to management, troubleshooting, and recovery infrastructure during an attack.
| Tip: Serial consoles with out-of-band (OOB) management provide an alternative path to systems and infrastructure that doesn’t rely on the production network, ensuring 24/7 management and recovery access during outages and other major incidents. OOB serial consoles can also be used to create an isolated recovery environment (IRE) where teams can safely restore and rebuild critical services without risking ransomware reinfection. |
4. Supply chain security
Organizations must implement supply chain security risk management measures to limit the risk of working with third-party suppliers. These include performing regular risk assessments based on the supplier’s security and compliance history, applying zero-trust access control policies to third-party accounts, and keeping third-party software and dependencies up-to-date.
| Tip: User and entity behavior analytics (UEBA) software uses machine learning to analyze account activity on the network and detect unusual behavior that could indicate compromise. It establishes baselines for normal behavior based on real user activity, reducing false positives and increasing detection accuracy even with vendors and contractors who operate outside of normal business hours and locations. |
5. Secure network and IT system acquisition, development, and maintenance
Entities must ensure the security of network and IT systems during acquisition, development, and maintenance. This involves, among other things, inspecting hardware for signs of tampering before deployment, changing default settings and passwords on initial startup, performing code reviews on in-house software to check for vulnerabilities, and applying security patches as soon as vulnerabilities are discovered.
| Tip: Automation can streamline many of these practices while reducing the risk of human error. For example, zero-touch provisioning automatically configures devices as soon as they come online, reducing the risk of attackers compromising a system-default admin account. Automated vulnerability scanning tools can help detect security flaws in software and systems; automated patch management ensures third-party updates are applied as soon as possible. |
6. Cybersecurity and risk-management assessments
Organizations must have a way to objectively assess their cybersecurity and risk-management practices and remediate any identified weaknesses. These assessments involve identifying all the physical and logical assets used by the company, scanning for potential threats, determining the severity or potential impact of any identified threats, taking the necessary mitigation steps, and thoroughly documenting everything to streamline any reporting requirements.
| Tip: An AI-powered cybersecurity risk assessment tool uses large language models (LLMs) and other machine learning technology to automate assessments with greater accuracy than older solutions. These tools are often better at identifying novel threats than human assessors or signature-based detection methods, and they typically provide automated reporting to aid in NIS2 compliance. |
7. Cybersecurity training
Essential and important entities must enforce cybersecurity training and basic security hygiene policies for all staff. This training should include information about the most common social engineering attacks, such as email phishing or vishing (voice phishing), compliant data handling practices, and how to securely create and manage account credentials.
| Tip: Some cybersecurity training programs include attack simulations – such as fake phishing emails – to test trainees’ knowledge and give them practice identifying social engineering attempts. These programs help companies identify users who need additional education and periodically reinforce what they have learned. |
8. Cryptography and encryption
NIS2 requires organizations to use cryptography to protect systems and data from tampering. This includes encrypting sensitive data and communications when necessary.
| Tip: Roots of Trust (RoTs) are hardware security mechanisms providing cryptographic functions, key management, and other important security features. RoTs are inherently trusted, so it’s important to choose up-to-date solutions offering strong cryptographic algorithms, such as Trusted Platform Module (TPM) 2.0. |
9. User access control and asset management
Entities must establish policies and procedures for employees accessing sensitive data, including least-privilege access control and secure asset management. This also includes mechanisms for revoking access and locking down physical assets when users violate safe data handling policies, or malicious outsiders compromise privileged credentials.
| Tip: Zero trust security uses network micro-segmentation and highly specific security policies to protect sensitive resources. MFA and continuous authentication controls seek to re-establish trust each time a user requests access to a new resource, making it easier to catch malicious actors and preventing lateral movement on the network. |
10. Multi-factor authentication (MFA) and encrypted communications
The final minimum requirement for NIS2 compliance is using multi-factor authentication (MFA) and continuous authentication solutions to verify identities, as described above. Additionally, entities must be able to encrypt voice, video, text, and internal emergency communications when needed.
| Tip: MFA, continuous authentication, and other zero-trust controls should also extend to management interfaces, resilience systems, and isolated recovery environments to prevent malicious actors from compromising these critical resources. The best practice is to isolate management interfaces and resilience systems using OOB serial consoles to prevent lateral movement from the production network. |
How ZPE streamlines NIS2 compliance
EU-based entities classified as essential or important have limited time to implement all the security policies, practices, and tools required for NIS2 compliance. Using vendor-neutral, multi-purpose hardware platforms to deploy new security controls can help reduce the hassle and expense, making it easier to meet the October deadline. For example, a Nodegrid serial console from ZPE Systems combines out-of-band management, routing, switching, cellular failover, SSL VPN and secure tunnel capabilities, and environmental monitoring in a single device. The vendor-neutral Nodegrid OS supports GuestOS and containers for any third-party software, including next-generation firewalls (NGFWs), Secure Access Service Edge (SASE), automation tools like Puppet and Ansible, and UEBA. Nodegrid devices have strong hardware Roots of Trust with TPM 2.0, selectable encrypted cryptographic protocols and cipher suite levels, and configuration checksumTM. Plus, Nodegrid’s Gen 3 OOB creates the perfect foundation for infrastructure isolation, resilience systems, and isolated recovery environments.
Looking to Upgrade to a Nodegrid serial console?
Looking to replace your discontinued, EOL serial console with a Gen 3 out-of-band solution? Nodegrid can expand your capabilities and manage your existing solutions from other vendors. Click here to learn more!