Out-of-Band Management vs FMEA: Bridging IT Recovery with Risk Mitigation

Out-of-Band Management vs FMEA: Bridging IT Recovery with Risk Mitigation
By Ahmed Algam
When it comes to mission-critical infrastructure, failure isn’t a possibility, it’s an eventuality. That’s why tools like FMEA (Failure Mode and Effects Analysis) exist in product validation and operational reliability.
But in IT, identifying risks isn’t enough. You have to be able to recover from them.
Let’s talk about where FMEA theory meets OOB (Out-of-Band) practice.
What is FMEA?
FMEA is a structured approach used to answer:
- What can fail? (Failure Mode)
- What happens if it does? (Effect)
- How likely is it to occur?
- How well can we detect or respond?
- What actions can reduce risk?
Each failure scenario is scored across three dimensions:
- Severity – How bad is the impact?
- Occurrence – How likely is it to happen?
- Detection – How easily can it be caught before causing damage?
The goal: Mitigate or eliminate high-risk scenarios before they cause downtime.
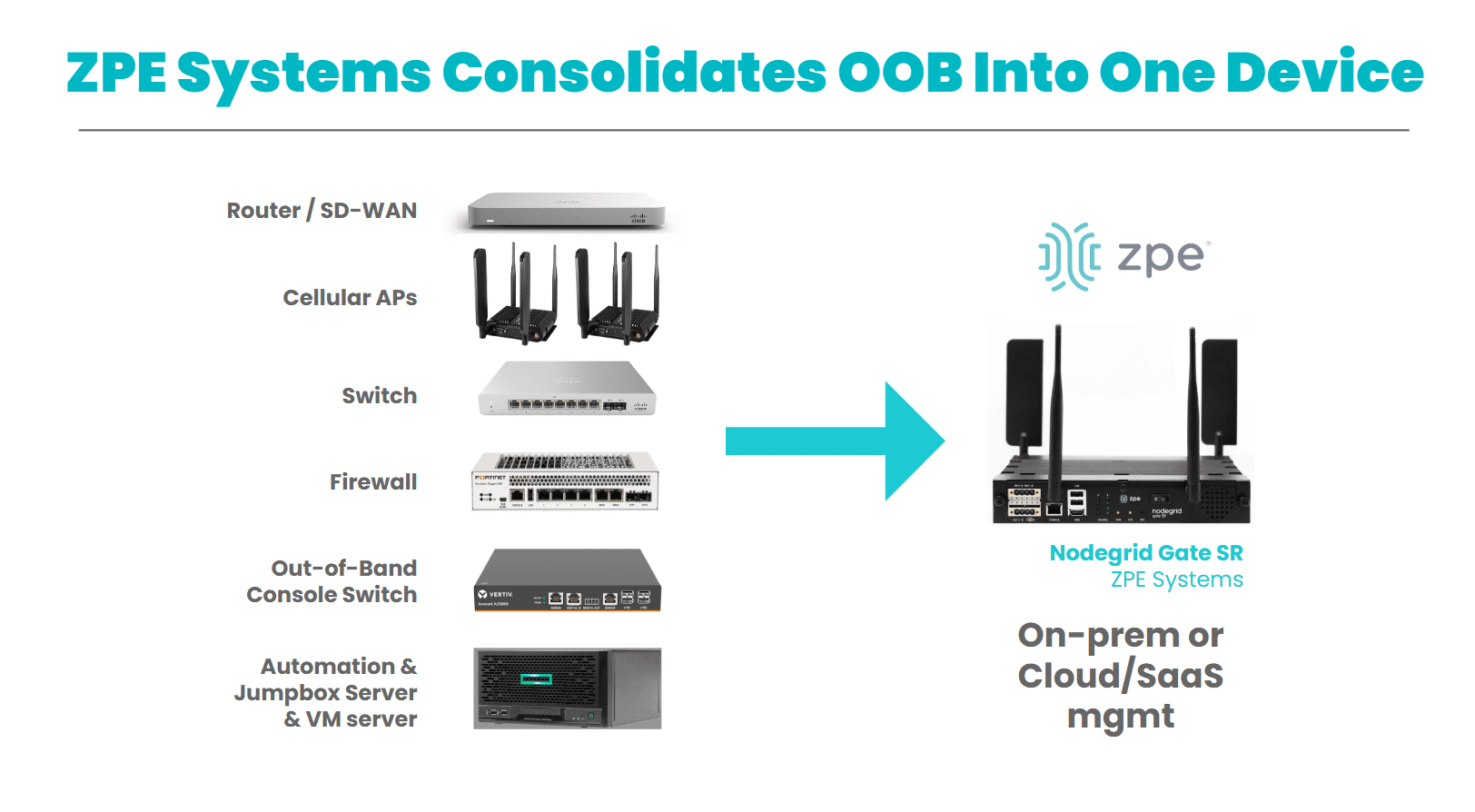
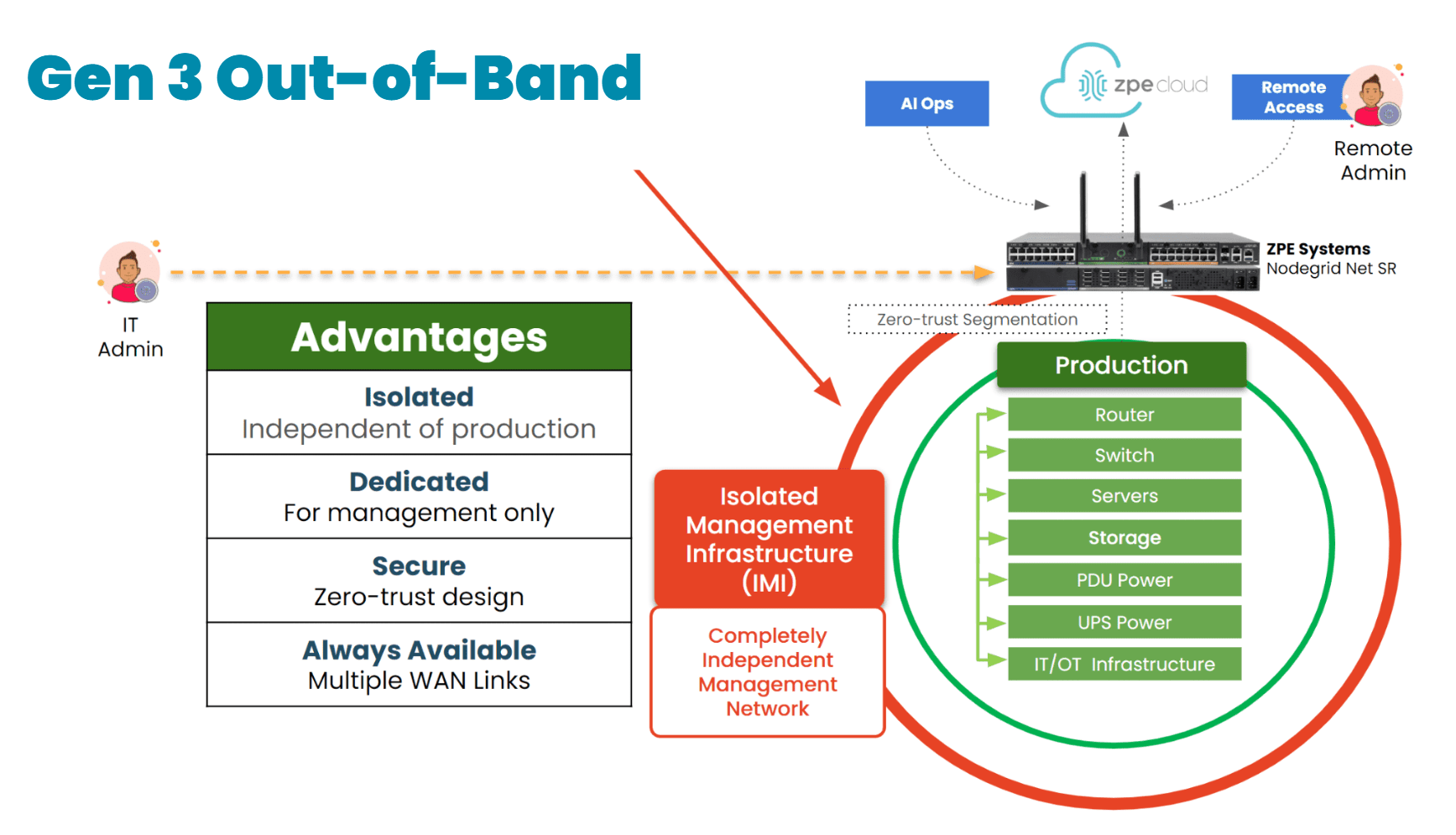
Where Out-of-Band Management Comes In
Now apply FMEA to IT infrastructure. Picture this:
- A router that locks up after a patch
- A firewall pushed with a bad config
- A top-of-rack switch that loses uplink
- A server stuck in BIOS after reboot
If your management tools are all in-band, you’re blind.
But with OOB, you keep access even when the network goes dark, using:
- 4G/5G LTE fallback
- Serial console access
- IPMI, Redfish, or BIOS-level control
- Out-of-band logging and alerting
How OOB Scores on the FMEA Scale
| FMEA Parameter | Out-of-Band Impact |
| Failure Mode | Network, power, or OS-level outage |
| Effect | Production outage, loss of remote access |
| Detection | OOB alerts via console logs, PDU telemetry, heartbeat monitoring |
| Occurrence | Reduced with safe, controlled remote management |
| Severity | Reduced since recovery actions are possible remotely |
| Control | Remote reboot, BIOS/IPMI access, serial console, file upload |
Real-World FMEA Meets Out-of-Band Management
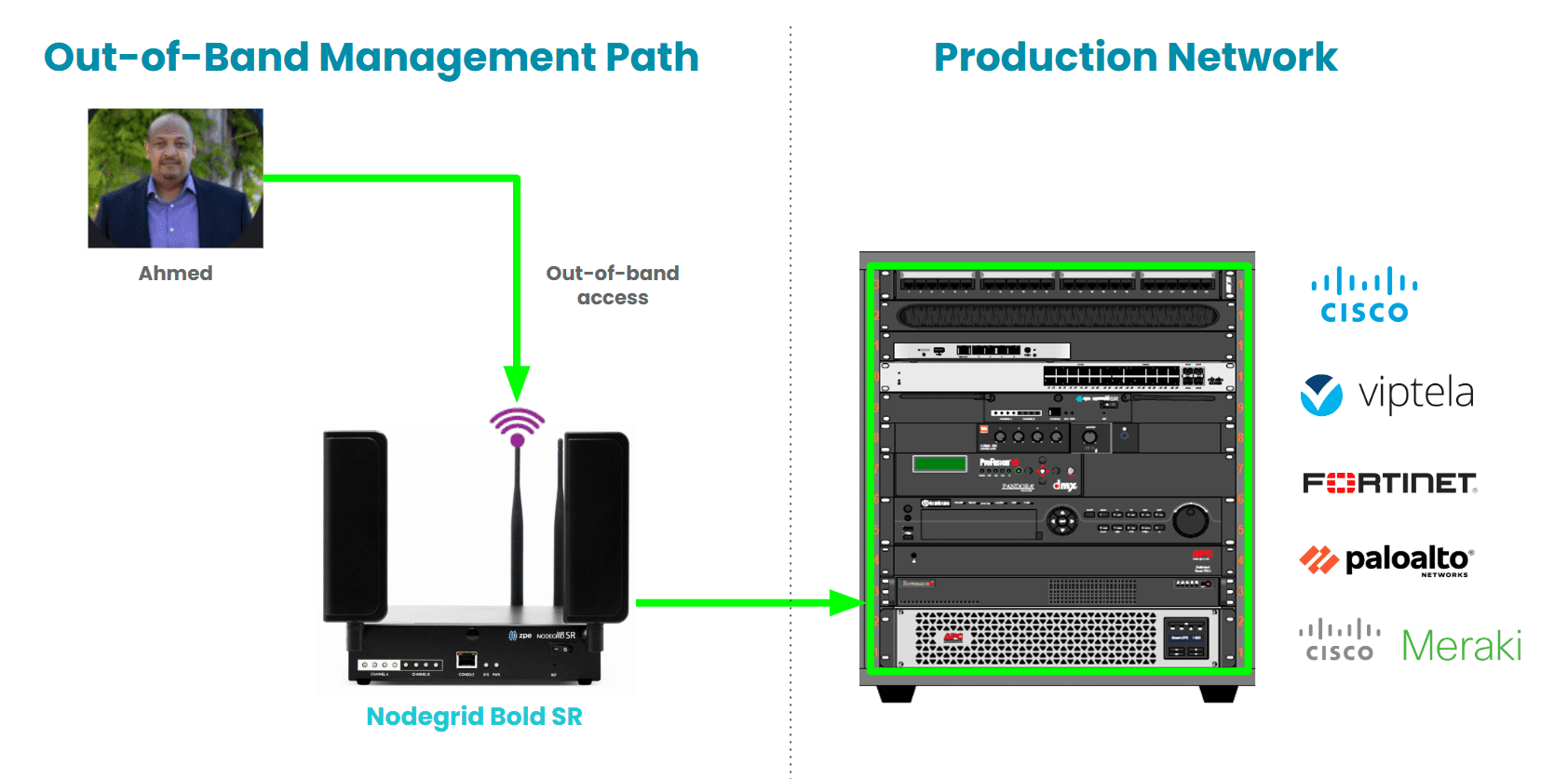
One customer thought they had OOB covered. They plugged a 4G modem into their Cisco router to allow remote access in case of failure.
But when the router failed, their “OOB” path failed with it because their monitoring agent was installed inside the network.
Once we showed them how to move the agent to the true OOB path (outside the primary network), it was an immediate “aha!” moment.
In FMEA terms:
They reduced Occurrence and improved Detection just by separating in-band from out-of-band.
Check out some more real-world stories like this one by reading my other article, 3 Real Lessons in Network Resilience.
Design for Recovery with ZPE
At ZPE Systems, we believe resilience starts with visibility and control, even when everything else fails. That’s the purpose of our Nodegrid platform:
- Secure, isolated access to remote infrastructure
- Cellular, Wi-Fi, and wired failover for real redundancy
- Integrations with top monitoring and automation platforms
- Smart, adaptive OOB architecture built to support FMEA-driven design
If Your FMEA Requires Recovery, We Can Help!
If your environment depends on high uptime, fast response, and remote visibility, Nodegrid is your bridge between failure analysis and real recovery.
Use the form below to contact us and let’s talk about your FMEA goals.